Microsoft Defender XDR is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. It is managed at https://security.microsoft.com/
There are a number of licensing options - check out Microsoft's documentation for information.
Configuration
Follow the instructions to install Defender on Workstations:
Follow the instructions to install Defender on Servers:
- Defender for Endpoint: Onboard servers
-
Defender for Identity: Onboard domain controllers
- The Azure Advanced Threat Protection sensor configurations vary depending on whether Endpoint or Identity is installed.
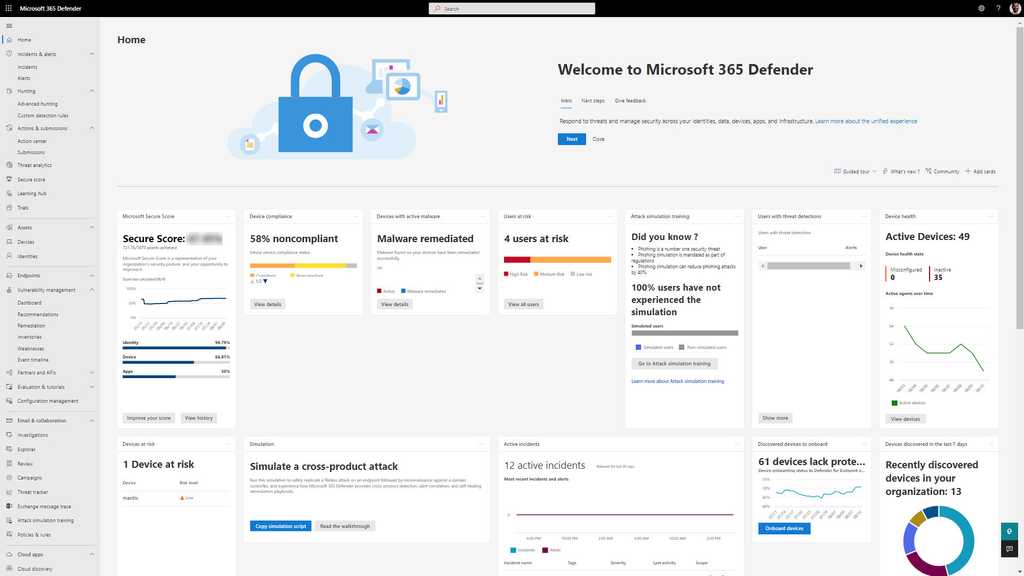
Secure Score
Microsoft Secure Score is a measurement of an organization's security posture, based on data from Defender for Endpoint and other Microsoft security products. It can be found at security.microsoft.com/securescore.
Points are given as per the following actions:
- Configuring recommended security features
- Remediating vulnerabilities
- Addressing the improvement action with a third-party application or software, or an alternate mitigation
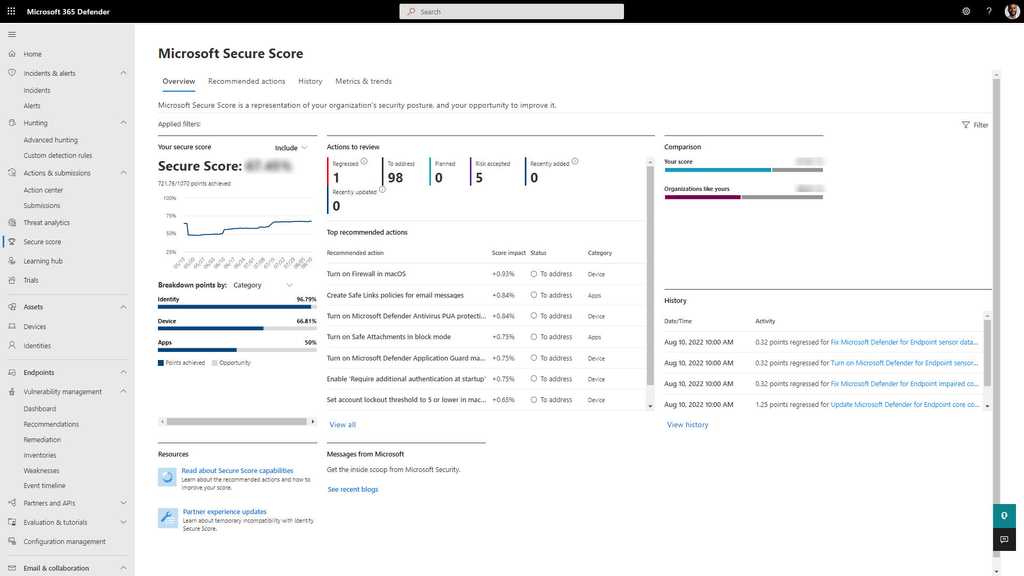
How to increase Secure Score
Each improvement activity is worth up to 10 points, based on their importance. Points are obtained by implementing security recommendations, such as updating software or configuring Intune policies (or GPOs) to secure user accounts and devices.
Security admins should check this score regularly and improve the score where possible.
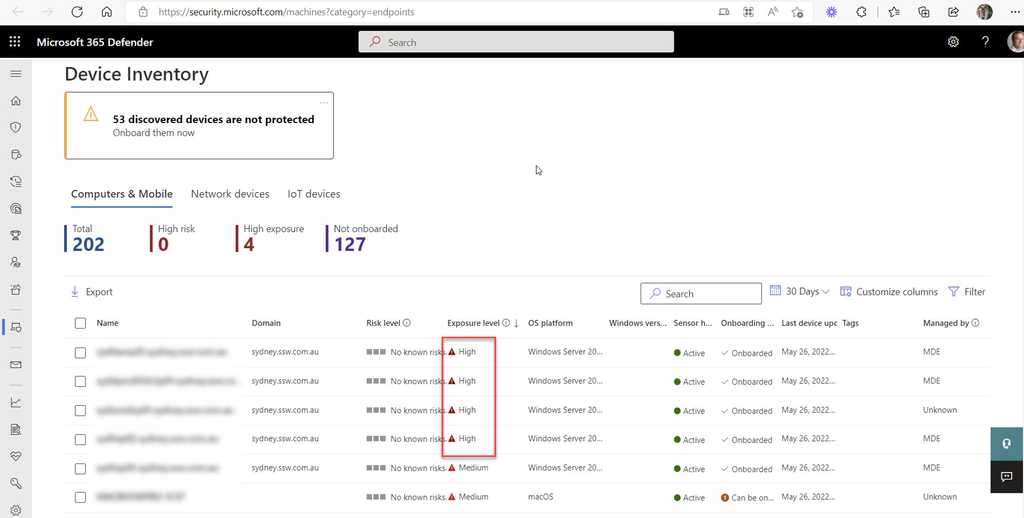
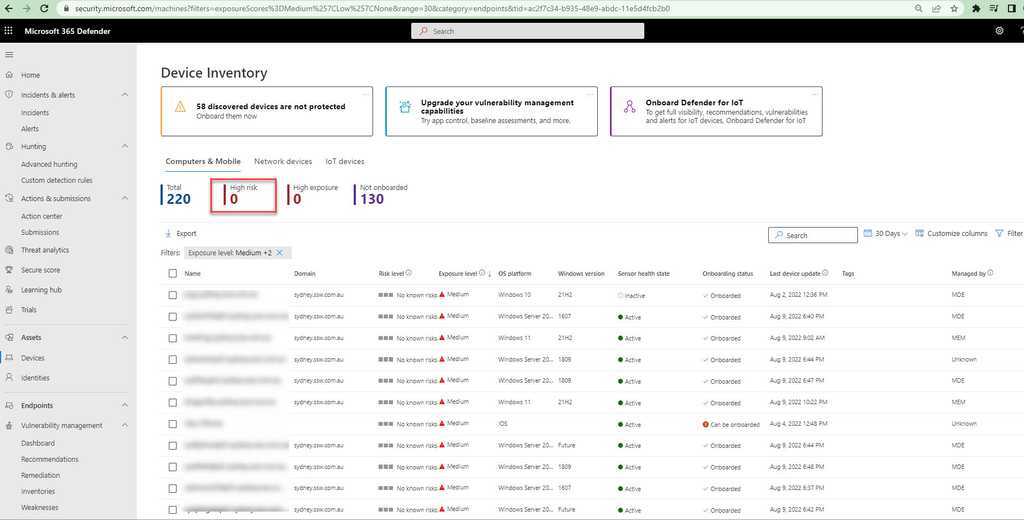
Device Inventory
Device inventory shows a list of the devices in your network. Devices are added to the device inventory through the Microsoft Defender for the Endpoint onboarding process. You’ll see information such as device name, domain, risk level, exposure level, OS platform, onboarding status, sensor health state, and other details for easy identification of devices most at risk.
Risk level reflects the overall risk assessment of the device based on combination of factors, including the types and severity of active alerts on the device. Resolving active alerts, approving remediation activities, and suppressing subsequent alerts can lower the risk level.
Exposure level reflects the current exposure of this device based on the cumulative impact of its pending security recommendations.
Security admins should check this page regularly and reduce the risk/exposure/criticality levels where possible.
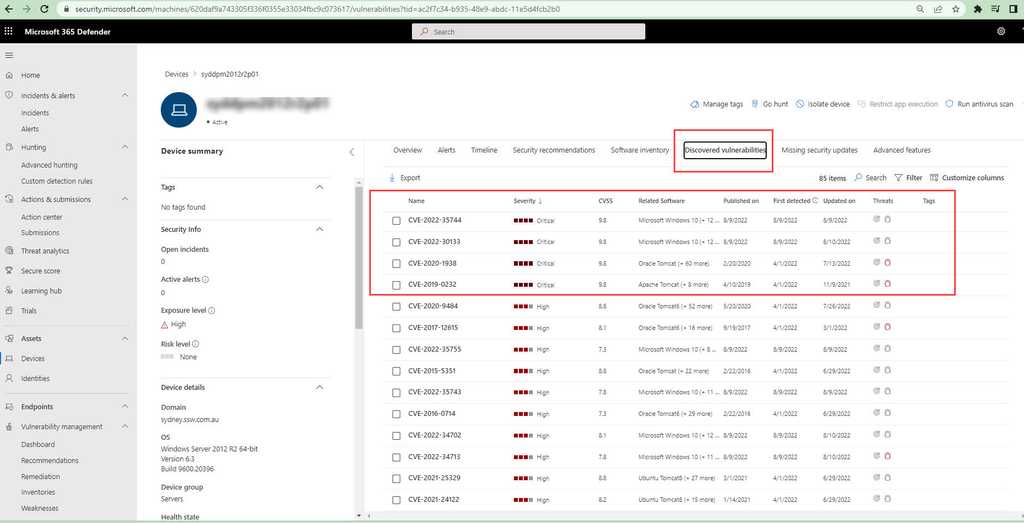
Security Recommendations
The Microsoft Defender portal has security recommendations for exposed devices which can be remediated manually after doing the needful (maybe a simple update): https://security.microsoft.com/security-recommendations/
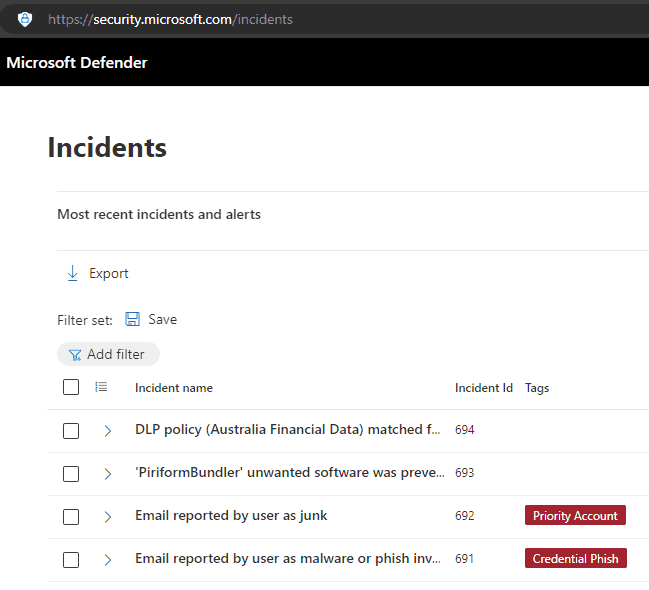
Incidents & Alerts
In Microsoft Defender XDR, an incident is a collection of correlated alerts and associated data that define the complete story of an attack. Defender for Office 365 alerts, automated investigation and response (AIR), and the outcome of the investigations are natively integrated and correlated on the Incidents page.
When critical incidents occur, you should receive an email notification so that you can act on the alert immediately.
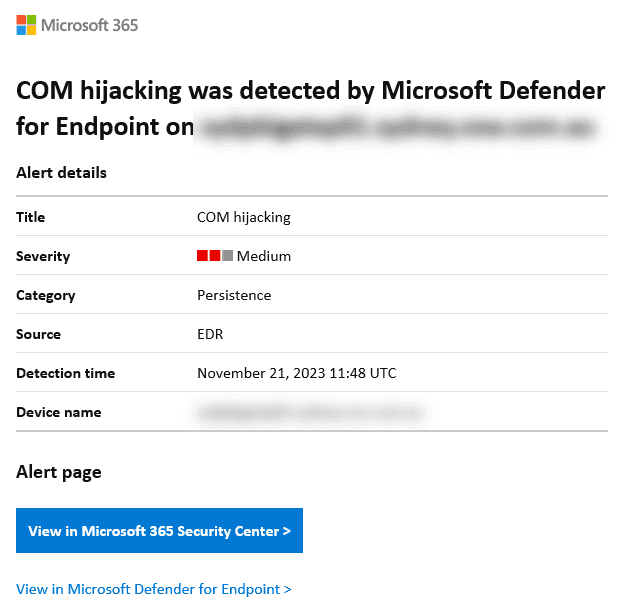
However, it is also important to check the Incidents page in Defender, to resolve less critical alerts - or email alerts that you may have missed. It is a good idea to set a reminder to check this page weekly.
These alerts can include emails that have been reported as malware or phishing, data loss prevention (DLP), or unwanted software detections.