Do you know how to recognize phishing URLs?
Last updated by Tiago Araújo [SSW] 10 months ago.See historyPhishing is a form of social engineering where an attacker tries to convince a victim that a resource they are in control of is a legitimate resource. This is usually achieved through the use of deceptive email messages or websites.
Attackers will often craft a website that looks like a legitimate one for the sole purpose of stealing your username and password (or some other sensitive information). They might, for example, build a website that looks exactly like LinkedIn, so that you think you are logging into LinkedIn, but are in fact giving an attacker your username and password.
A URL is made up of a fully-qualified domain name (FQDN) and a path. The FQDN is the part between the https:// and the next /. Anything after the / is part of the path and not the FQDN.
The FQDN is made up of a top-level domain (TLD), a domain, and then a subdomain or subdomains. These move from right to left, so for the address https://www.ssw.com.au/, .com.au is the TLD, ssw is the domain, and www is a subdomain.
For the address https://www.ssw.com.au/people/, people is the path. The path can include all kinds of other characters and parameters.
You should always check that the domain matches the service or website you are expecting.
http://linkedin.com.sggr.ru/someaddress
Bad example – The address has LinkedIn in it, but it is a sub-domain, not the domain
http://linked-in-hq.com/linkedin/myprofile
Bad example – The address has LinkedIn in it, but it is in the path, not the FQDN. The FQDN is also suspicious
http://linkedinalerter.com
Bad example – The address has LinkedIn in it, but is not a legitimate LinkedIn site
https://linkedin.com/someaddress
Good example – LinkedIn is a secure domain
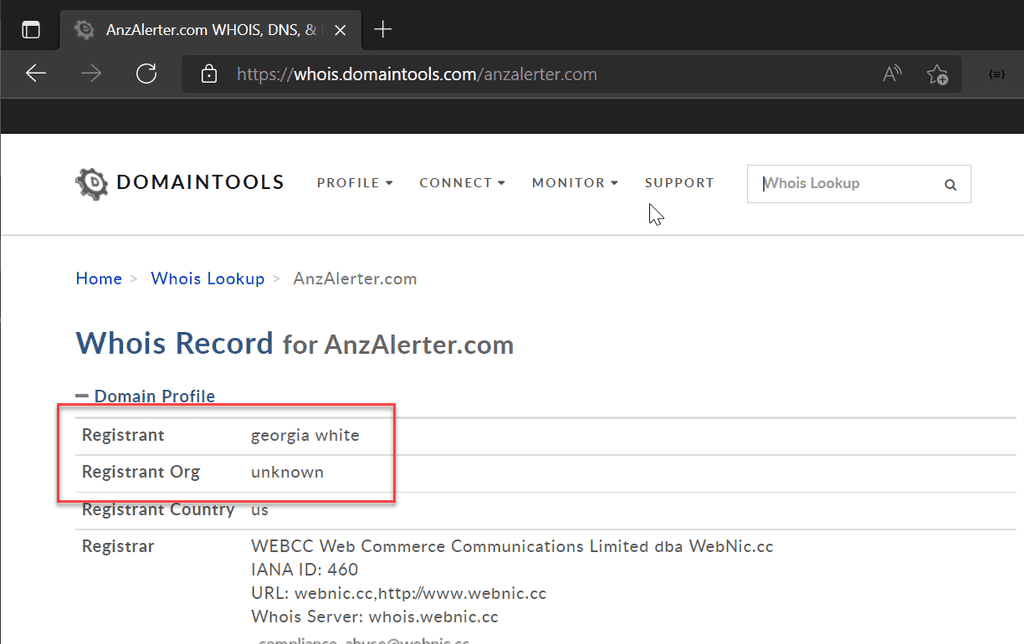
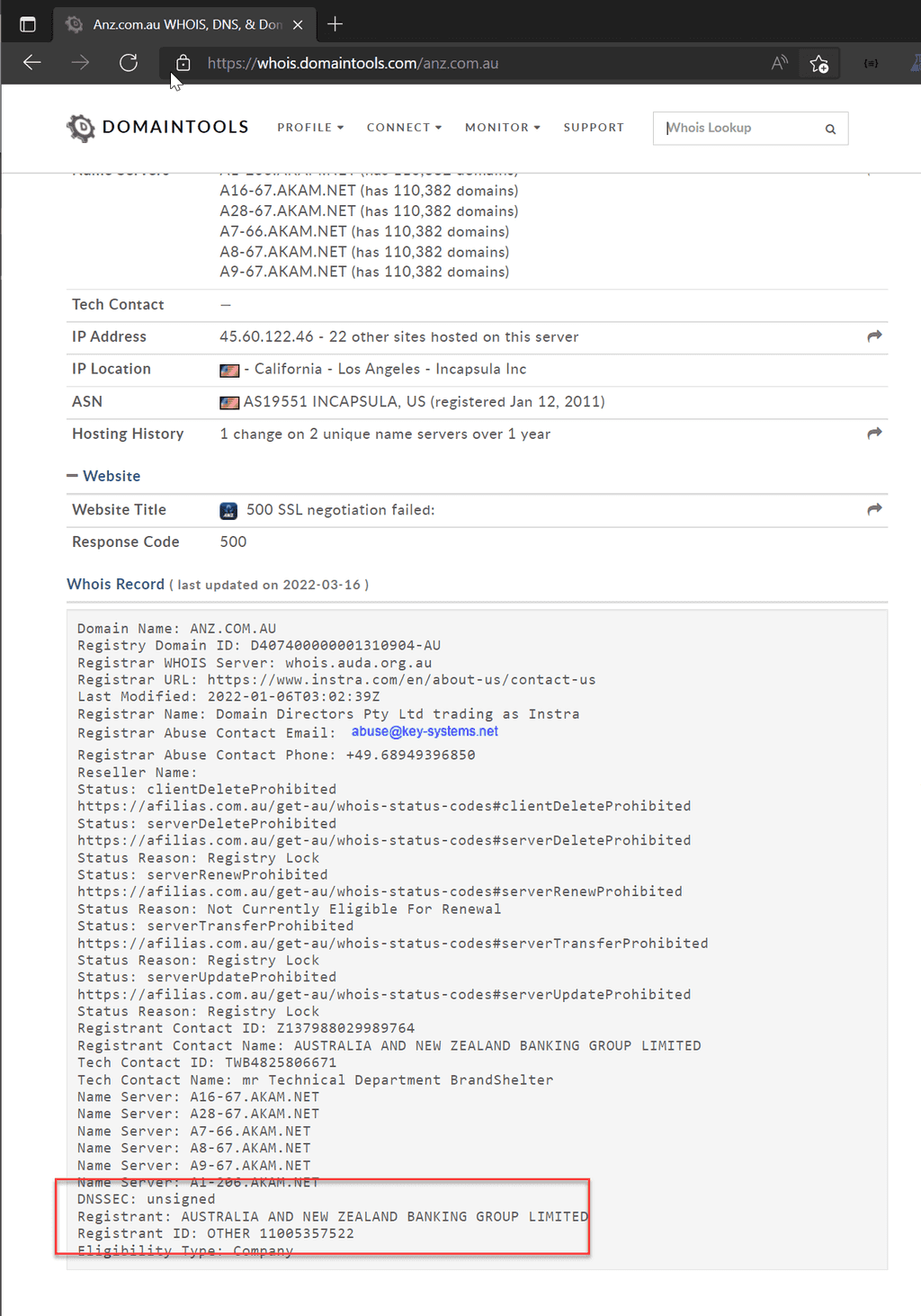
If you are curious about a URL, and think it might be legitimate, you can check the Whois record to see who owns the domain.