Rules to Better Active Directory - 16 Rules
Optimize your Active Directory management by adding staff profile pictures for better visibility and disabling users instead of deleting them for improved CRM reporting. Standardize group names, utilize Group Policy for settings, enable auditing of logon attempts, and manage local administrator passwords with LAPS to enhance security and efficiency.
You can upload staff profile pictures into Active Directory. Exchange and Lync will automatically use these profile pictures.
Using a free third party tool AD Photo Edit tool which can be downloaded from cjwdev.co.uk you can upload staff profile pictures into AD. You need to run the application with Domain Admin rights. After you have uploaded the picture for a user it will take some time for the change to be replicated through to Exchange and Lync if you have use these solutions.
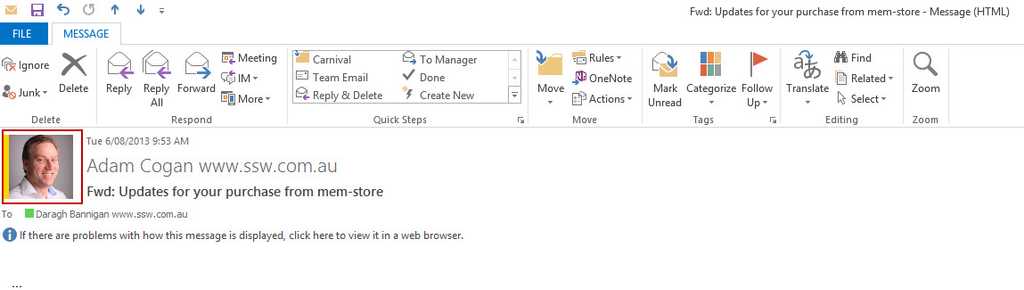
Figure: Profile picture imported from AD into Exchange 
Figure: Profile picture imported from AD into Lync When a user is created in Active Directory (AD), a Global Unique Identifier (GUID) is also created. As the name suggests this is unique for each user and is never duplicated in a domain.
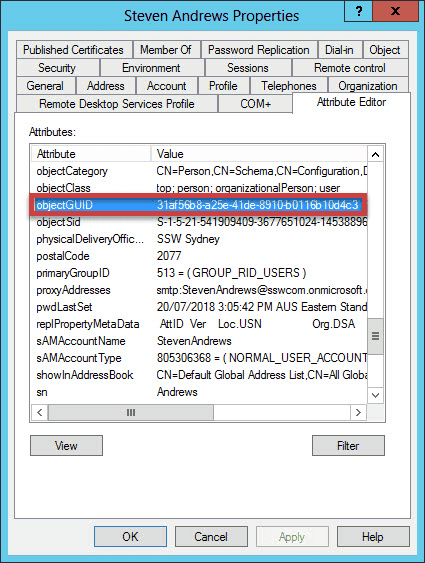
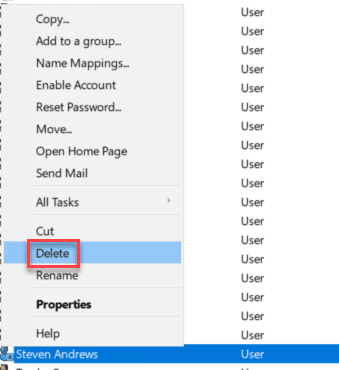
Figure: GUID for User Steven Andrews When adding a user to CRM, they are assigned with an Employee ID that is linked to the AD account’s GUID.
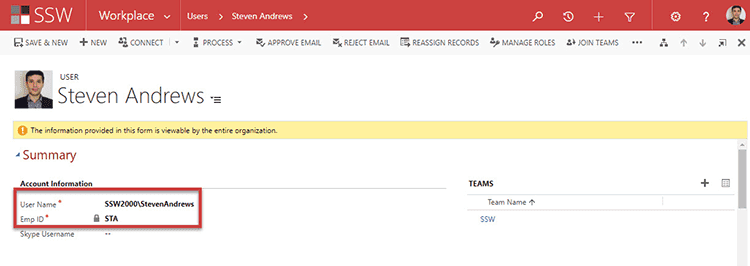
Figure: AD User StevenAndrews is tied to STA Employee ID through AD GUID When a user leaves, many companies go through the process of disabling the CRM account and then deleting the AD User.
This creates problems if the employee comes back to the company and a new AD account is created for them - they are no longer able to be associated with the previously created CRM account. Instead, they will need a new CRM user with a different Employee ID.
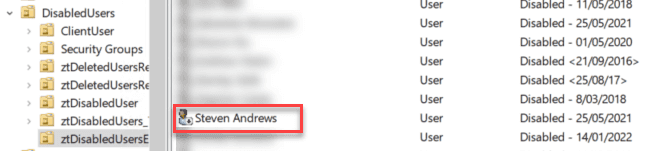
This makes reporting on a user that has returned more difficult. To get around this problem, it is better to disable and move the user to a "Disabled Users" OU in AD, so that if they return, the AD and CRM user can just be re-enabled.
What is a postmaster account?
It is an RFC mandated specification email address use to identify the administrator of a mail server. Any errors in email processing are directed to the postmaster address.
The email received at this address is sent to the mail server administrator, in our case the SysAdmins.
At SSW we have configured postmaster@ssw.com.au as a distribution group, with mail server administrators as members of this distribution group.
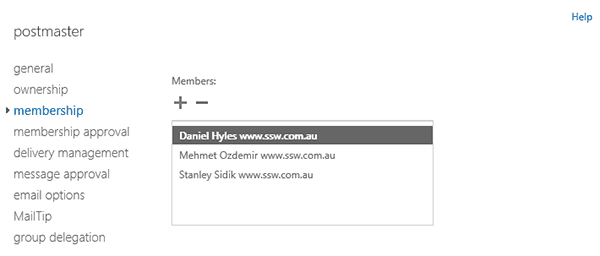
Figure: Group members of postmaster@ssw.com.au The use of standardized group names is a simple yet crucial step towards easier management. Reducing the number of AD groups will make it simpler to manage and allow new staff to figure out what's what faster.
You can save yourself countless confused conversations by standardizing AD Group Names.
Warning: Be very careful if you are renaming groups - permissions can break, especially if the group is sync'd to Entra ID (formerly Azure AD).
For example, this is a list of AD groups associated with products:
SSWSugarLearningAlerts
Alerts CodeAuditor
SEC_SSW-LinkAuditor-Devs
timepro-devsFigure: Bad Example – With no consistency, it is difficult to know the correct name for an AD group
SSWSugarLearningAlerts
SSWCodeAuditorAlerts
SECSSWLinkAuditorDevs
SECSSWTimeProDevsFigure: Good Example – By standardizing the names of AD groups it saves confusion
Note: For large organizations, a better way is to use a type of group (eg. Local or Global)... then the entity it is associated to… then the resource (or service).
Examples:
- L-LocalGroupName-SYD-EntityName-SP-Sharepoint- becomes L-SYD-SP-SSW-Users
- G-GlobalGroupName-SYD-EntityName-SP-Sharepoint- becomes G-SYD-SP-SSW-Users
Types of groups
It is also important to differentiate between Distribution groups (or other groups with mail enabled), and Security groups. Distribution groups should have names that are clear, that work well for an email address - for example, SSWRulesDevs. Security groups should have the prefix It is SEC_, so that it is clear they are security groups (and cannot receive email), e.g. SEC_VPNUsers.
Group Policy is simply the easiest way to reach out and configure computer and user settings on network based on Active Directory Domain Services (AD DS). If your business is not using Group Policy, you are missing a huge opportunity to reduce costs, control configuration, keep users productive and happy, and harden security. Think of Group Policy as "touch once, configure many."
You can manage all aspects of Group Policy by using the Group Policy Management Console (GPMC). You start the GPMC from the Start menu: Click Start, All Programs, Administrative Tools, Group Policy Management. You can also click Start, type Group Policy Management, and then click Group Policy Management in the Programs section of the Start menu. Windows Server 2008 onwards include the GPMC when they are running the AD DS role.
Figure: Group Policy Management Console showing GPO
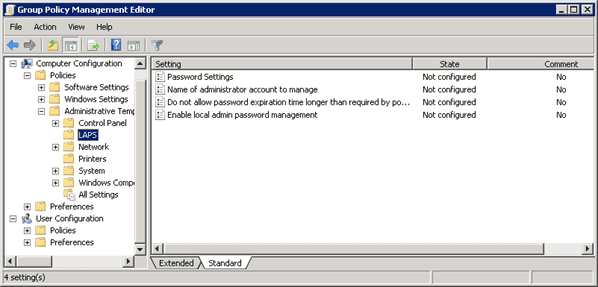
It is important as a Network Administrator to know when and where failed login attempts are coming from. Through Group Policy you can enable "Audit logon events".
- Create a group policy called 'Logon Auditing Policy'
- Right click on 'Logon Auditing Policy' and click on Edit to bring up Group Policy Management Editor
- Select 'Audit account logon events' from Computer Configuration | Policies | Windows Settings | Local Policies | Audit Policy and set to Success, Failure
- Select 'Audit logon events' from Computer Configuration | Policies | Windows Settings | Local Policies | Audit Policy and set to Success, Failure
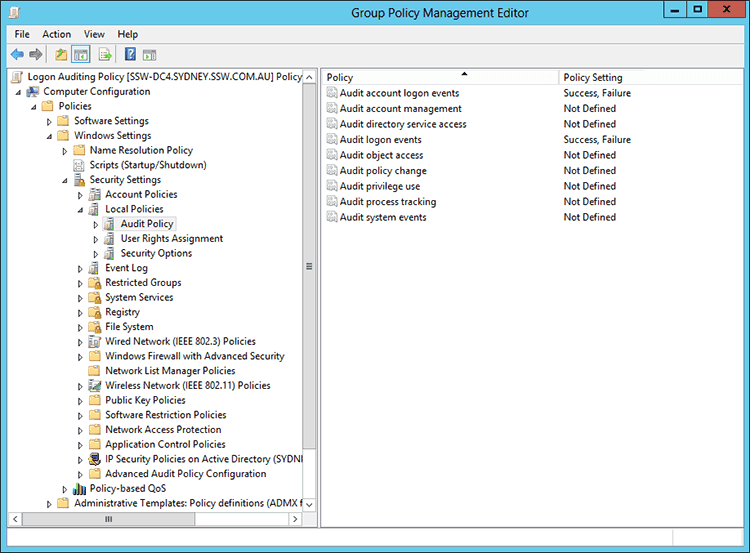
Figure: Select 'Audit logon events' - Select 'Audit: Force audit policy...' from Computer Configuration | Policies | Windows Settings | Local Policies | Security Options and set to Enabled
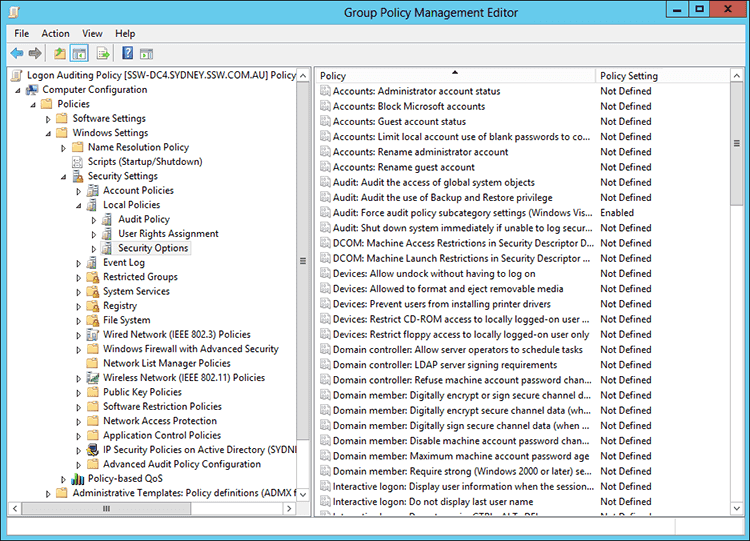
Figure: Select 'Audit: Force audit policy...' 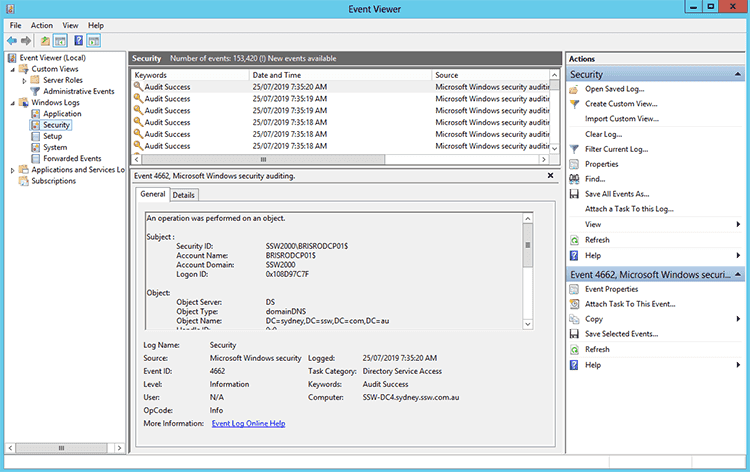
Figure: Successful and Failed login attempts will now appear in Event Viewer | Security
Now when you will have access to seeing success/failed login attempts on user accounts, these can then be captured and audited with your own internal process or a third party application such as Whats Up Gold, see: Do you monitor failed login attempts?Group Policy is a fast and effective way to configure Hibernate on multiple PC's.
To enable Hibernate option in Group Policy open up Group Policy Management.
- Create a new Group Policy Object and name it "EnableHibernate"
- Right click on "EnableHibernate" and click on Edit to bring up Group Policy Management Editor
- Select 'Show hibernate in the power options menu' from Computer Configuration | Policies | Administrator Templates | Windows Component | File Explorer and set to Enabled
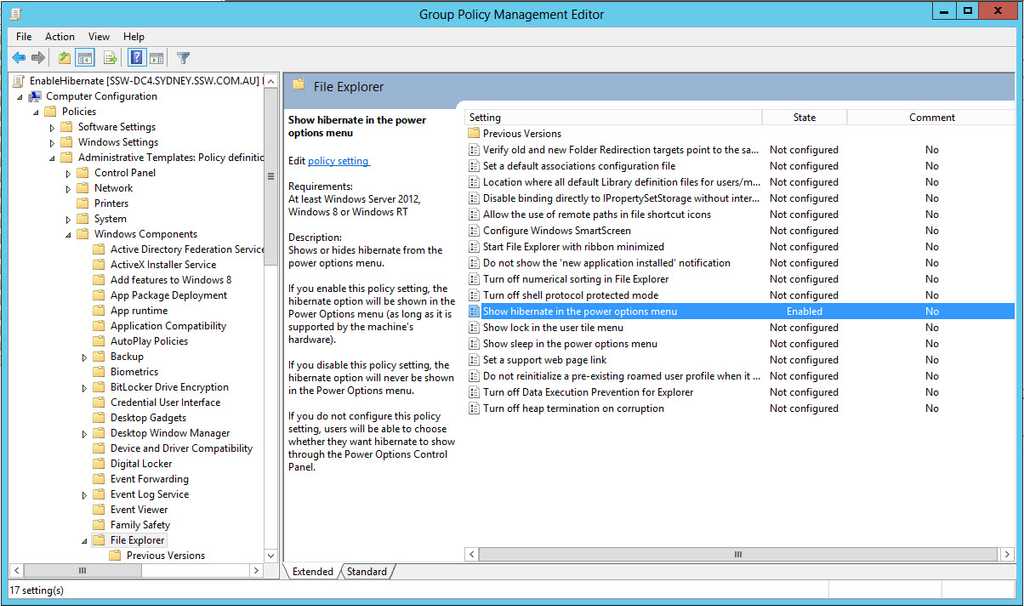
- Back in Group Policy Management Enable Link for "EnableHibernate"
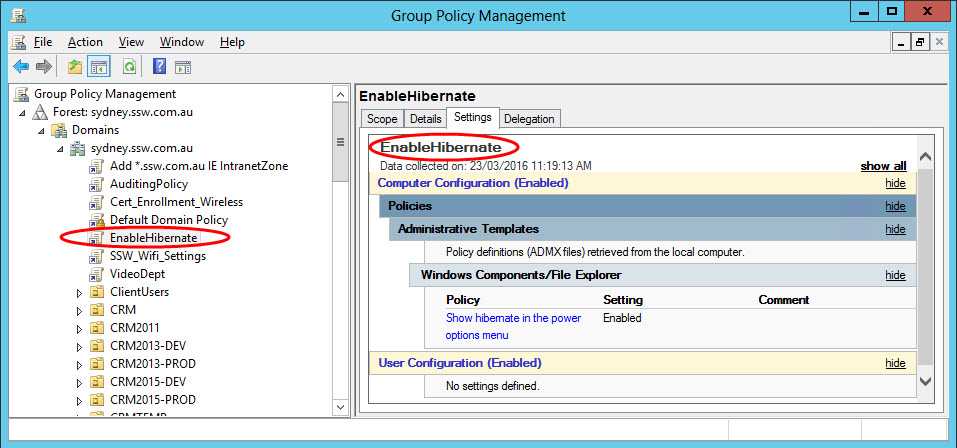
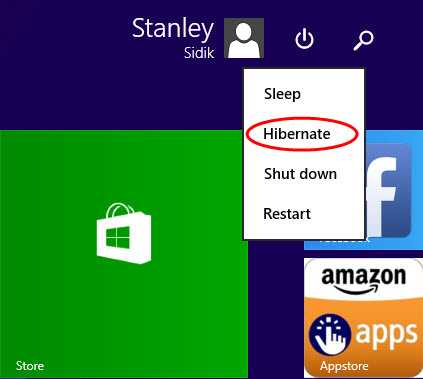
- Wait for a few moment for GPO to refresh and apply. Alternatively manually force a GP Update through Command Prompt - GPUpdate /force. Check that Hibernate Option is now in Start Menu
When using a single account for normal user login and admin tasks the first thing that comes to mind is all of the Group Policy settings associated with that account. This could include scripts, software installations, drive mappings, printers and many other settings that would apply when you log on to a computer in the domain. You wouldn’t want all of these to apply when log on to a Domain Controller of any other servers.
Another reason is you may step away from your computer and forget to lock the computer. This will expose your computer for your co-workers and tinker with your system and as a consequence if that account has domain administrator privilege they can change system security and settings on any Domain Controller and other servers.
To prevent this, at SSW we create a separate Administrator account, with the prefix Admin. This signifies that it is an Admin account and does have administrator privileges. The Admin account is also placed in a separate OU to ensure that it is not receiving unnecessary Group Policies. This allows us to setup permissions easier, only provide access to machines required, and also makes the user aware that they are doing something dangerous so they are inheritably more careful. A standard account (Non Admin prefix account) does not and should not have access to any servers.
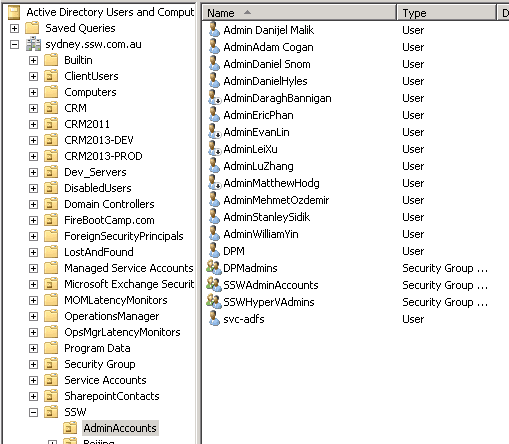
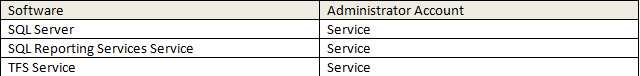
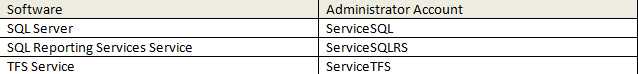
Figure: SSW AD Users and Computers showing Admin accounts in separate OU When using service accounts, you should have a specific AD account for each major service.
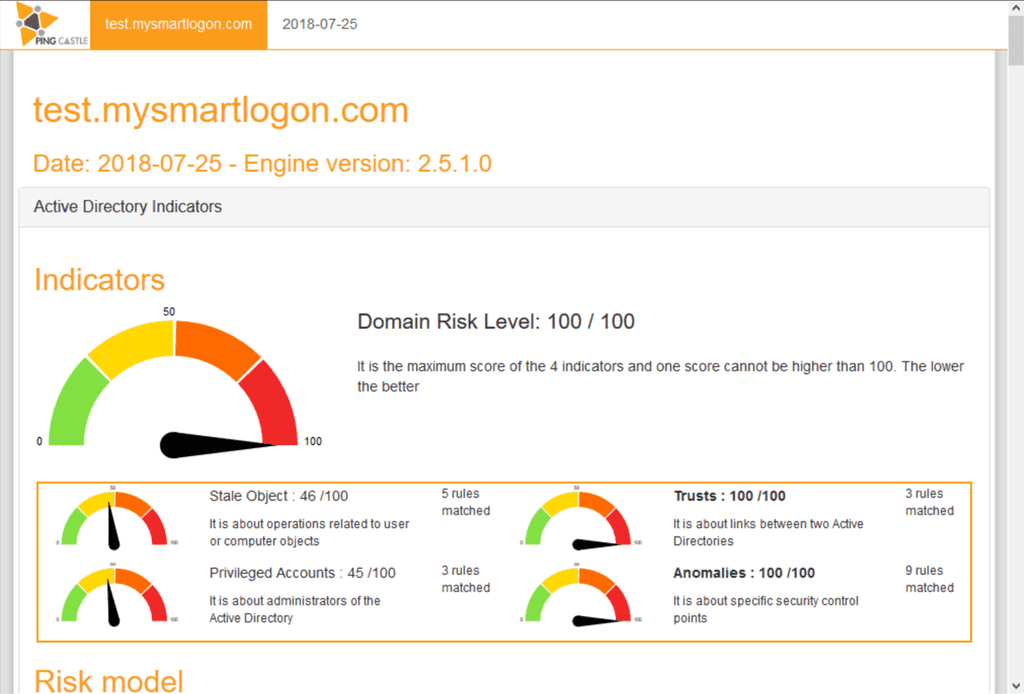
"Active directory is quickly becoming a critical failure point in any big sized company, as it is both complex and costly to secure..." - PingCastle
PingCastle is an Active Directory auditing tool. It checks your accounts, computers and configuration in AD and gives you a great report on things that should be addressed. It is a tool that should be run periodically - every 3-6 months - to keep AD secure.
PingCastle is easy to install and run - see their documentation for more information. It is free to use in your own environment, or there are paid versions for MSPs and larger enterprises.
Once you have run it, you get a great report on your Active Directory security health, with detailed recommendations of what you need to fix.
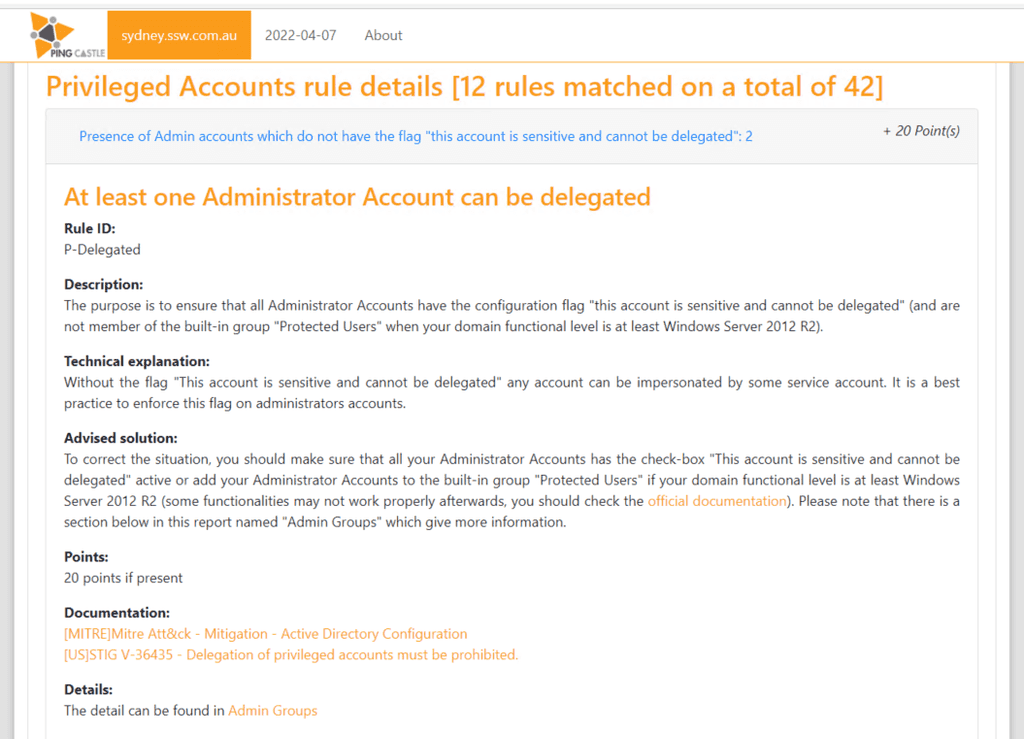
Figure: Example item from PingCastle, with detailed description and solution It is important to know what to do with your employees' accounts when they leave. Getting this wrong can create security vulnerabilities - or it can make life difficult for everyone if the employee comes back to work for you again.
From a System Administrators point of view
You should create a list of instructions that are followed whenever an employee leaves so that the experience is consistent for all and to make sure you don't miss any steps. Here are some important ones - you will need to add more to suit your environment.
- Change their mailbox to a shared mailbox and check if the email count in the inbox is near 0 (to be done with their manager)
- Inspect their personal devices such as mobile phones to ensure that company Data has been removed and OneDrive is also removed as per the security measures
-
Power Automate flows - Remove ex-employees from the primary owner and add someone else who is eligible to own the flow
a. Change the owner - Click on Edit | Under owner remove yourself | Add someone else who is eligible to own the flow
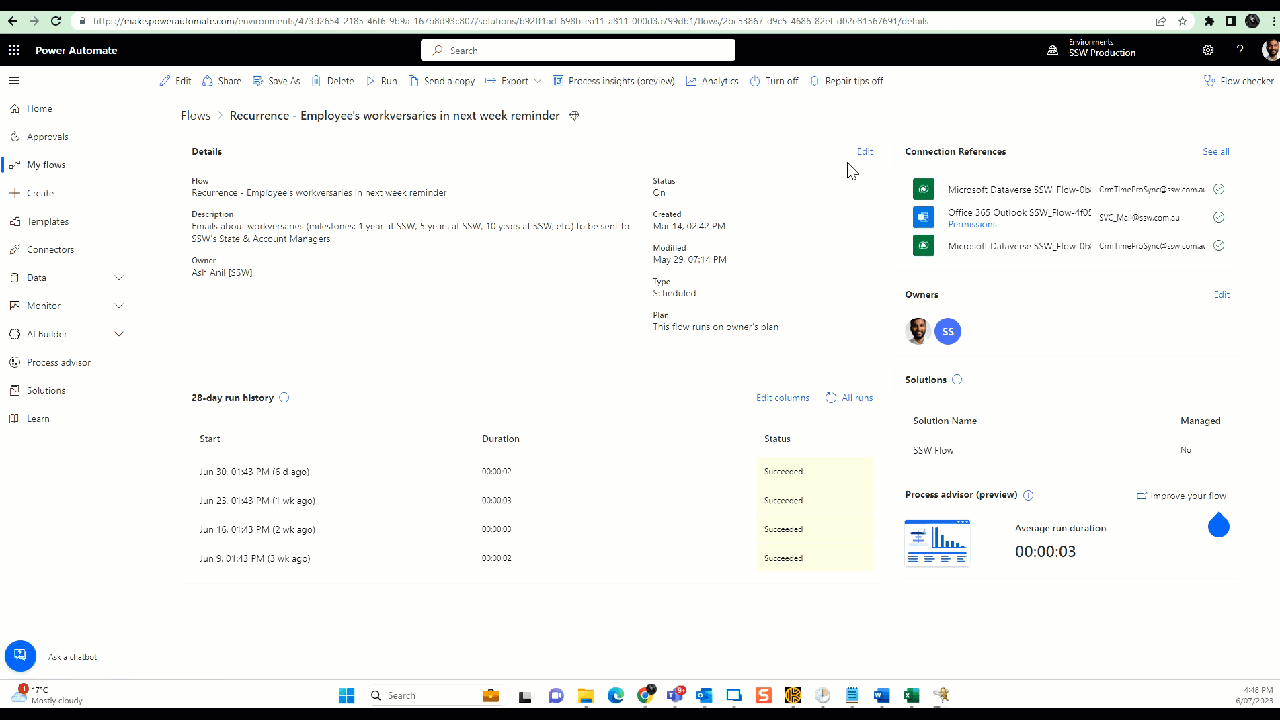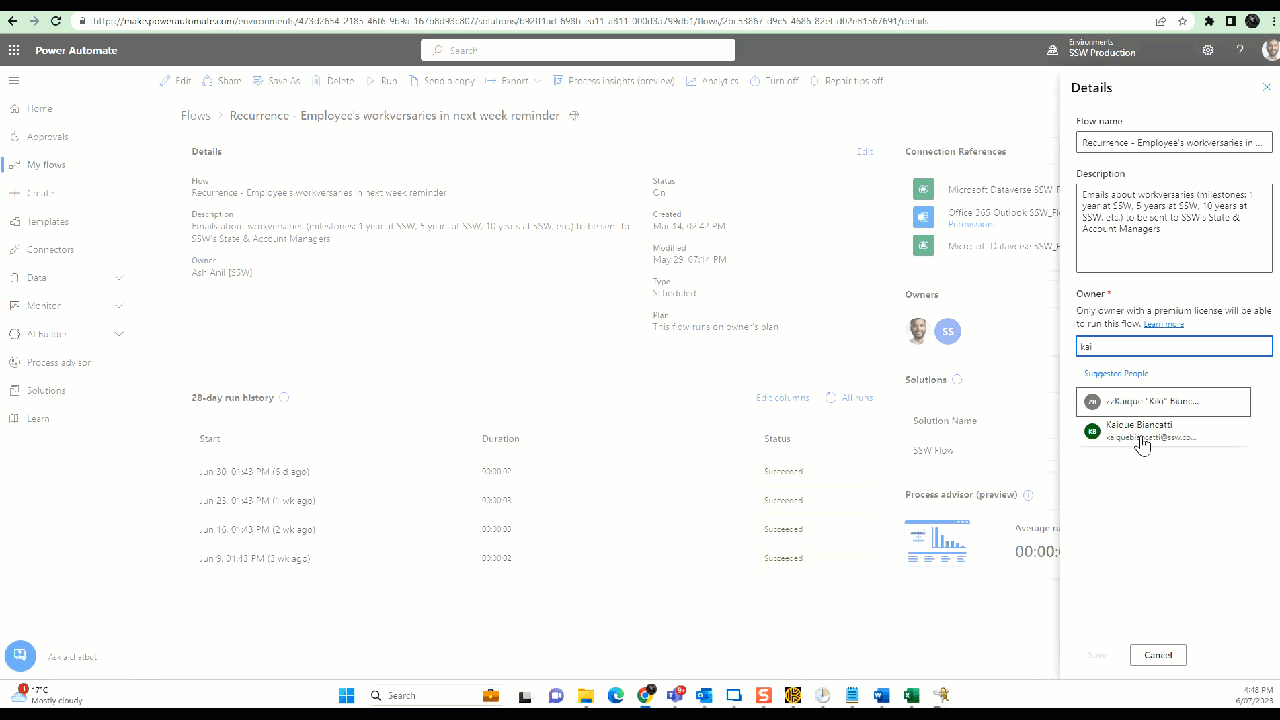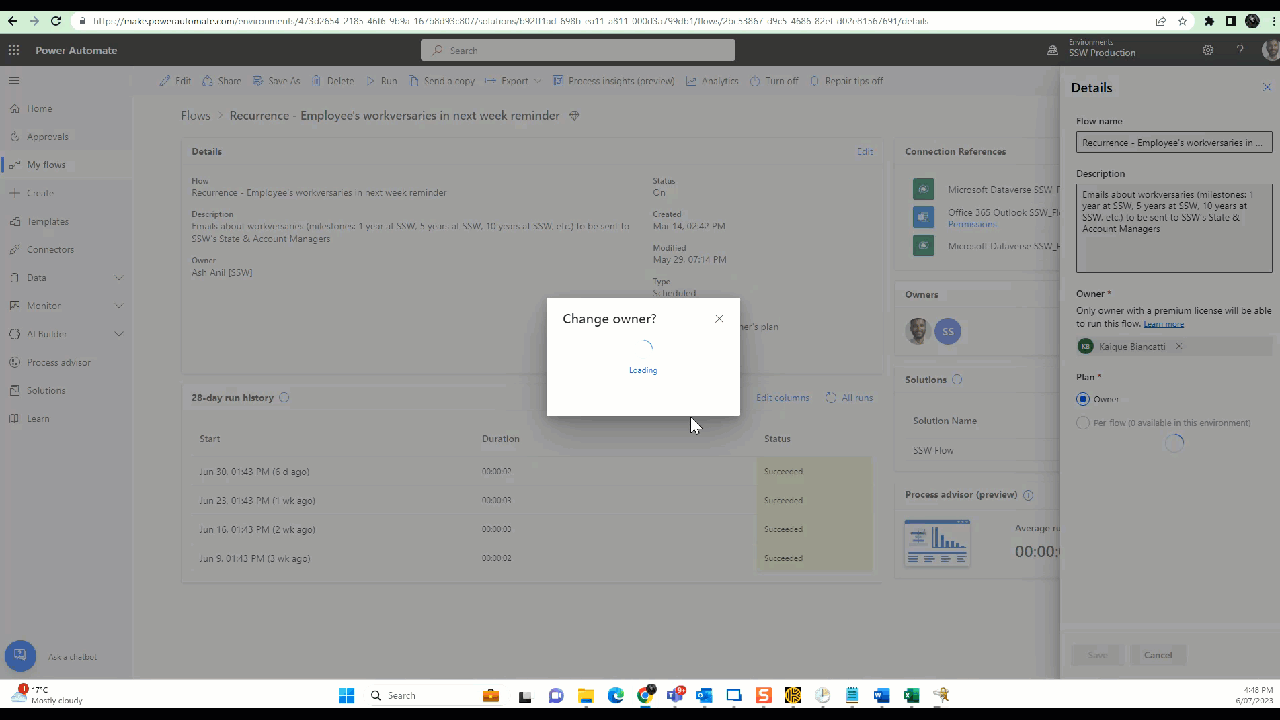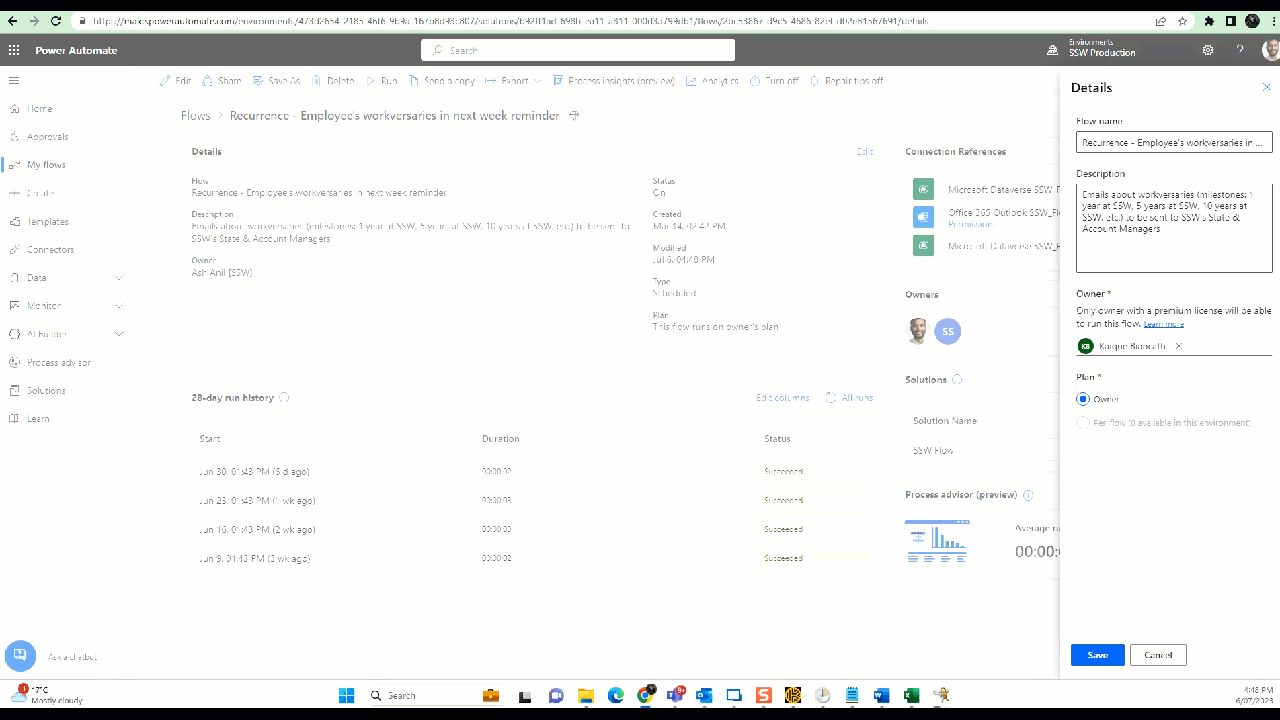
Figure: Power Automate Flow - Change primary owner b. Share all the flows with System Administrators and any other groups - Click Share | Type in "Groups you want to share" under Owners | Click OK
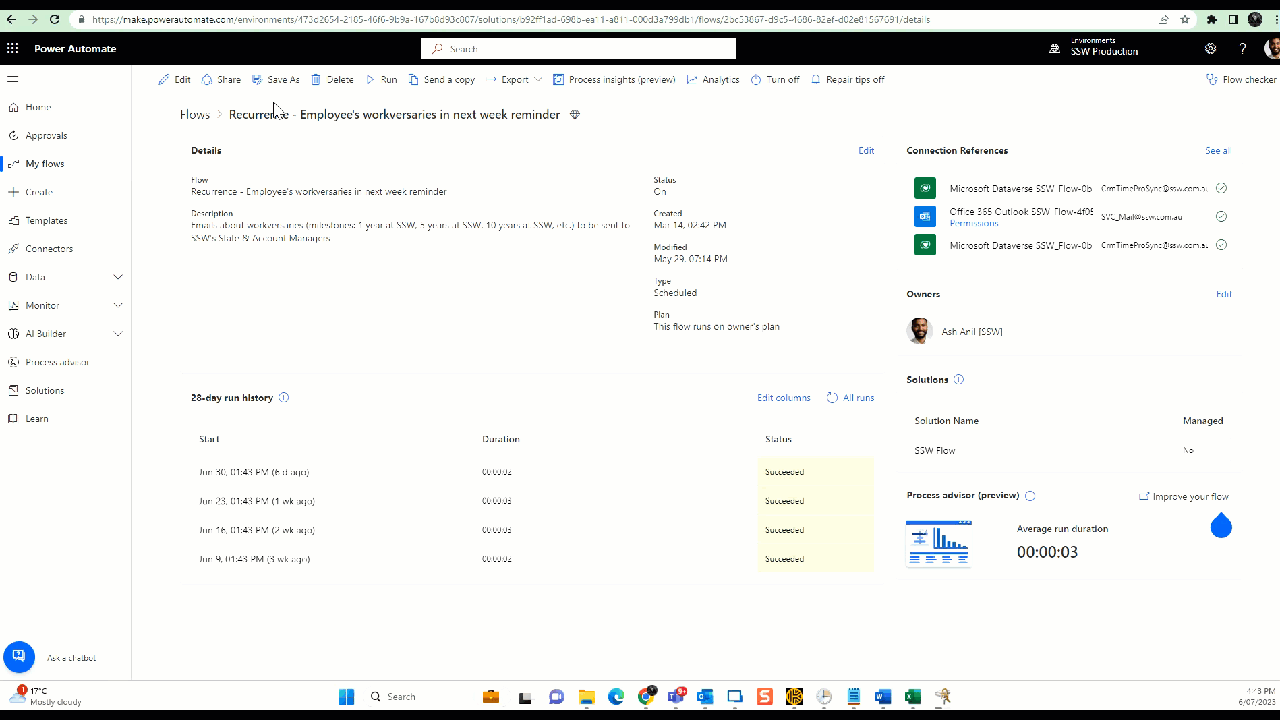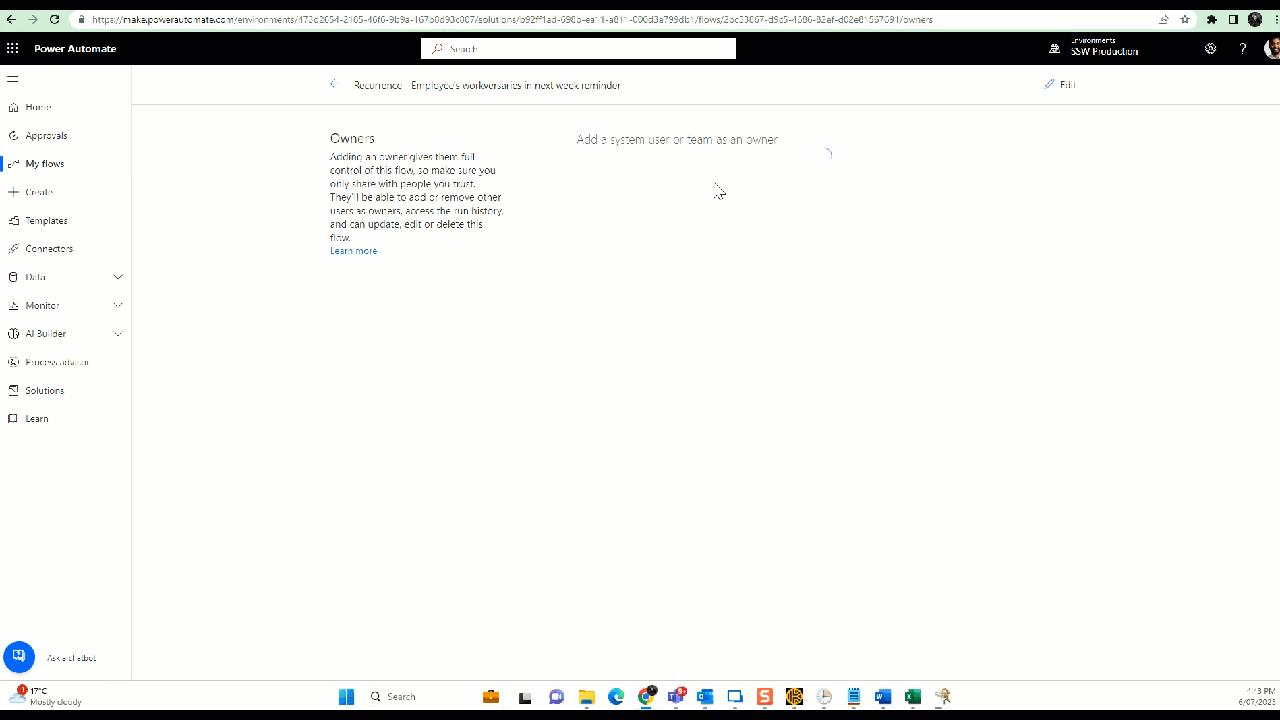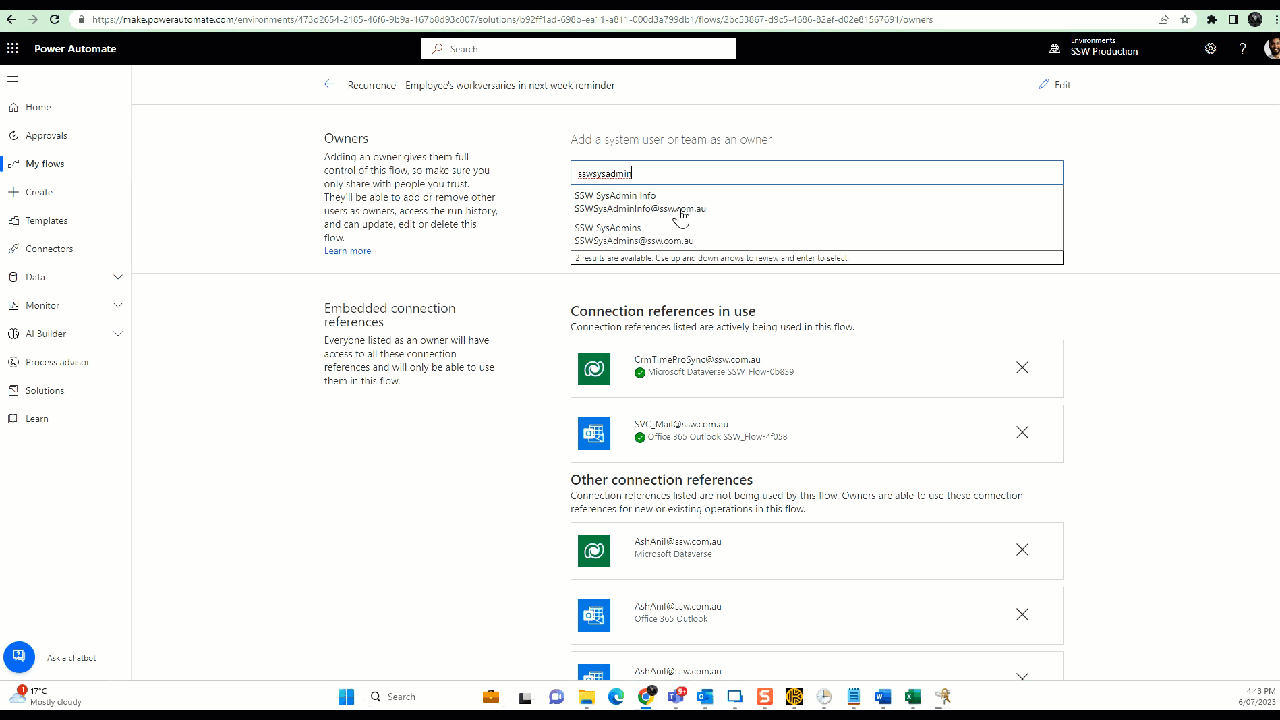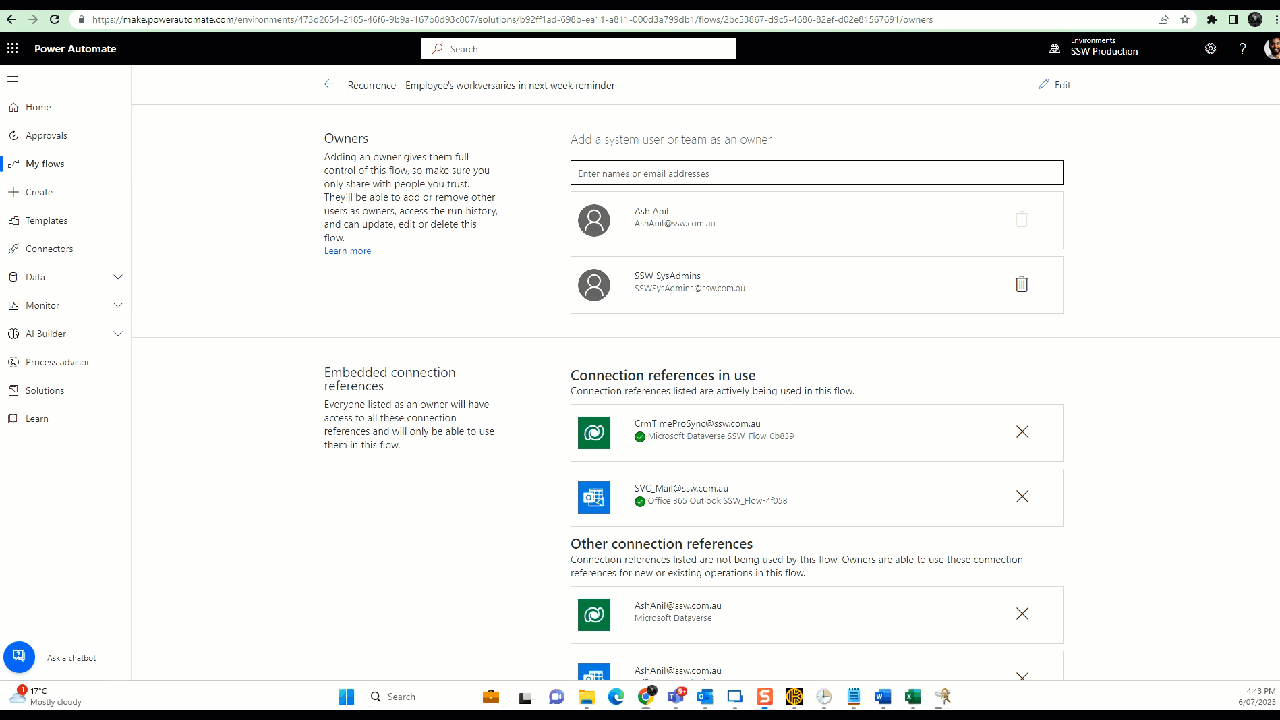
Figure: Power Automate Flow - Share with SysAdmins -
Backup data. Make sure you have a backup of the employee's work. This might include:
- Check their mailbox, Teams, OneDrive, etc. are in your Email backup solution
- Alternatively, export their Outlook PST file
- Files from their computer
- Remove their AD user account from any group membership
-
Disable their AD account - and any other accounts they have:
- Move their account to a "disabled users" OU
- Don't delete their account, this can cause issues in the future!
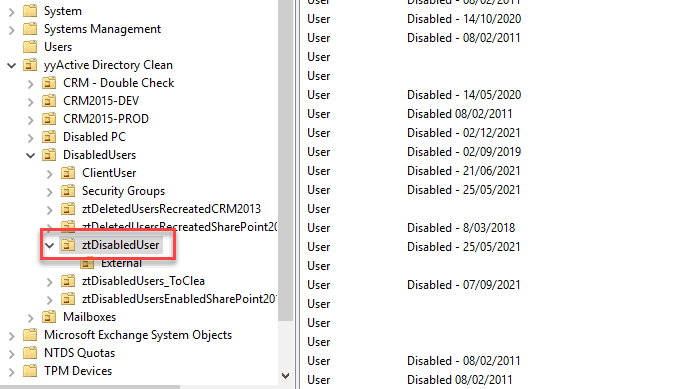
Figure: Disabled User OU - Forward their emails to another employee
- Make sure they return any IT equipment they have and delete their computer account/s from AD
- Remove any security/automation access
Keeping your Active Directory environment tidy is helpful to keep things running smoothly, but it is also important to improve your security posture.
Computer accounts in AD are similar to user accounts - they can be used to access other systems and data in your domain. Since computer accounts do not hold any useful information, it is safe to delete them when a computer is decommissioned. It is also very easy to re-join a computer to the domain if needed, so there is no reason to leave computers in a "disabled" state.
Keeping your Active Directory (AD) environment secure is paramount for your overall security posture, so it is important to keep track of changes that are made in AD - and to have alerts for when potentially damaging changes are made.
Auditing your Active Directory environment with third-party tools offers several advantages. While this can be done with a SIEM such as Splunk or Microsoft Sentinel, these might be overkill for some companies.
There are dedicated tools just for AD Auditing, such as ManageEngine ADAudit Plus. Let’s delve into the benefits of using such tools, focusing on visibility, alerting, and reporting:
1. Enhanced Visibility
Third-party AD auditing tools provide deeper insights into your environment. They allow you to track changes, monitor user activity, and understand permissions more comprehensively. Here’s how enhanced visibility benefits your organization:
- Granular Tracking: These tools capture detailed information about user logon/logoff activity, group membership changes, and modifications to AD objects. You gain visibility into who did what and when
- Real-Time Monitoring: With real-time monitoring, you can detect suspicious or unauthorized activities promptly. Whether it’s an unexpected privilege escalation or an unusual login pattern, these tools keep you informed
- Identifying Stale Accounts: By identifying inactive or stale accounts, you can improve security and reduce clutter in your AD environment
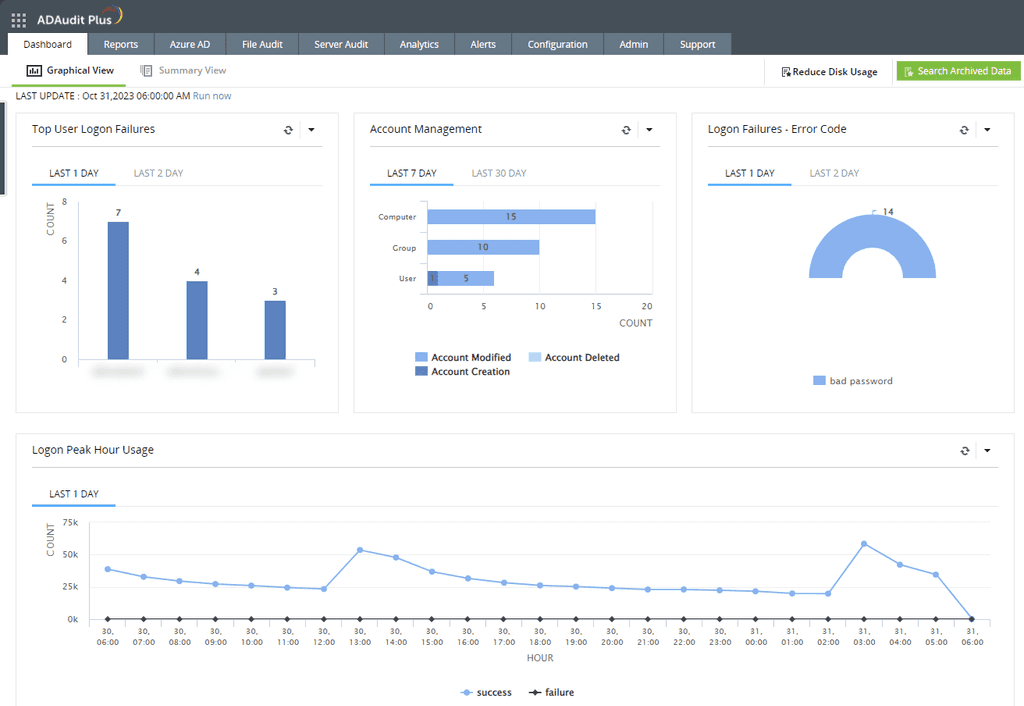
Figure: ADAudit Plus Dashboard gives you immediate visibility 2. Proactive Alerting
Effective alerting mechanisms are crucial for timely incident response. Third-party AD auditing tools offer customizable alerts based on specific events or conditions:
- Threshold Alerts: Set thresholds for critical events (e.g., failed logins, privilege changes). When these thresholds are exceeded, receive alerts via email or other channels
- Privileged Group Changes: Get notified when users are added to or removed from privileged groups (e.g., Domain Admins). This helps prevent unauthorized access
- Suspicious Behavior: Receive alerts for unusual patterns, such as multiple failed logins or access from unexpected locations
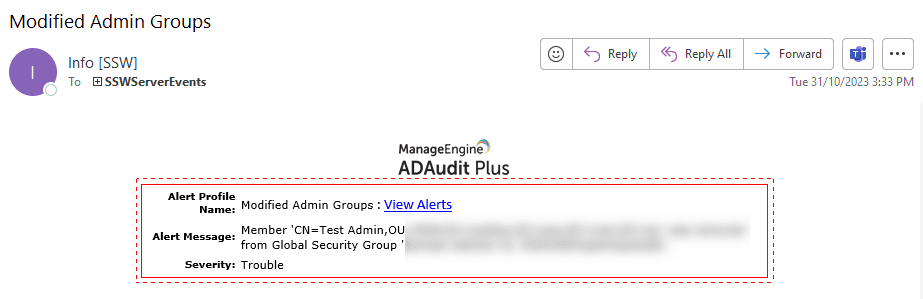
Figure: Email alert from ADAudit Plus 3. Comprehensive Reporting
Reporting is essential for compliance, audits, and management decision-making. Third-party tools provide pre-built reports and customizable templates:
- Change Reports: Track modifications to AD objects (users, groups, OUs) over time. Examples include user creation/deletion, password changes, and group membership updates
- Security Reports: Assess security settings across your AD environment. Identify vulnerabilities like weak passwords or excessive permissions
- Compliance Reports: Generate reports aligned with industry standards (e.g., PCI DSS, HIPAA). Demonstrate adherence to regulations
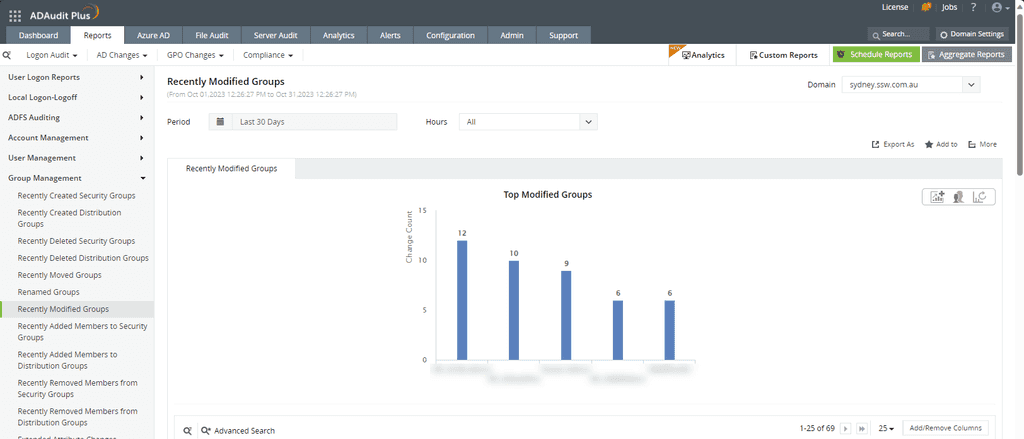
Figure: ADAudit Plus gives you 100's of reports - for example, recently modified groups Third-Party Tools
Here are some examples of notable third-party AD auditing solutions:
-
- Offers comprehensive auditing capabilities for AD
- Tracks changes in real-time
- Provides pre-built reports and customizable dashboards
-
SolarWinds Access Rights Manager
- Covers compliance audits and permission auditing
- Enhances AD management with time-saving features
-
- Offers change management features
- Provides detailed reports on AD changes
Remember that the choice of tool depends on your organization’s specific needs, budget constraints, and scalability requirements. Evaluate different options to find the best fit for your environment!
To detect and mitigate a cyber attack, the right set of events need to be collected from your domain controllers. The audit policy is a compromise between collecting too many and too few events. Logs are useful for detecting security events, but if there is too much noise, you'll miss the important information.
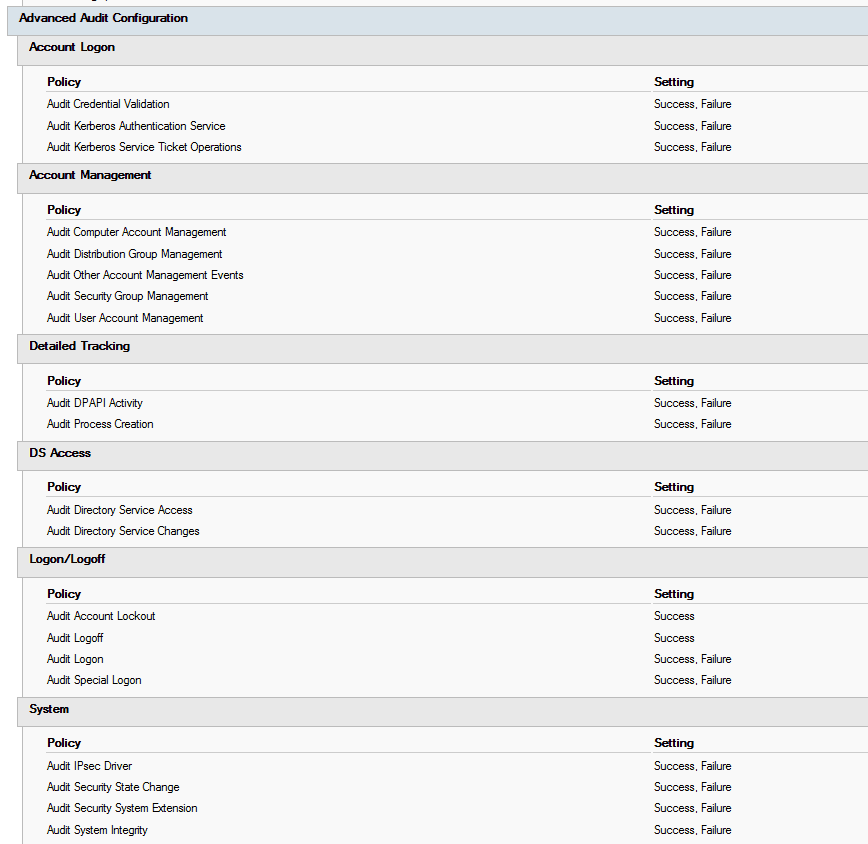
To enable advanced auditing on your domain controllers, use group policy. The settings are in Computer Configuration | Windows Settings | Security Settings | Advanced Audit Policy Configuration | Audit Policies.
adsecurity.org has great recommendations for what you should be auditing on your domain controllers (as well as a heap of other useful information!). Here is their list:
-
Account Logon
- Audit Credential Validation: Success & Failure
- Audit Kerberos Authentication Service: Success & Failure
- Audit Kerberos Service Ticket Operations: Success & Failure
-
Account Management
- Audit Computer Account Management: Success & Failure
- Audit Other Account Management Events: Success & Failure
- Audit Security Group Management: Success & Failure
- Audit User Account Management: Success & Failure
-
Detailed Tracking
- Audit DPAPI Activity: Success & Failure
- Audit Process Creation: Success & Failure
-
DS Access
- Audit Directory Service Access: Success & Failure
- Audit Directory Service Changes: Success & Failure
-
Logon and Logoff
- Audit Account Lockout: Success
- Audit Logoff: Success
- Audit Logon: Success & Failure
- Audit Special Logon: Success & Failure
-
System
- Audit IPsec Driver: Success & Failure
- Audit Security State Change: Success & Failure
- Audit Security System Extension: Success & Failure
- Audit System Integrity : Success & Failure
See the list in context, and more information here: https://adsecurity.org/?p=3377
-
It is best practice to limit the number of administrator accounts in your environment, including local administrators on users' computers. However, it is necessary to have a local administrator account so the computer can be accessed if it loses connection to the domain. LAPS does exactly that.
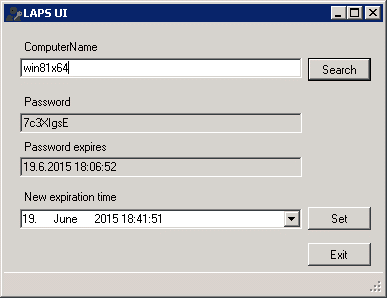
Microsoft LAPS provides management of local account passwords of domain or hybrid-joined computers. Passwords are stored in on-premises Active Directory (AD) or Entra ID and protected by ACL or RBAC, so only eligible users can read it or request for it to be reset. The passwords are automatically changed regularly - the default is every 30 days, but this can be changed. LAPS is provided by Microsoft and comes integrated with newer Windows versions.
As of April 2023, Microsoft has launched a new solution called Microsoft LAPS which replaces the older Windows LAPS.This updated version of LAPS brings some much needed features:
- Cloud native - You can back up passwords to Entra ID
- Security - Passwords are encrypted in AD (they weren't in legacy)
- History - Password change history is now recorded
If you still have legacy OSs (e.g. Windows Server 2016, older Windows 10/11 versions) in your fleet, you can have the new and legacy LAPS working in parallel with clever Group Policies applying to those systems, as the new LAPS does not work with them.
Microsoft LAPS (new)
The new LAPS is integrated directly into Windows and does not need any install or downloads to work, you only need to be at least in the April 11 2023 Update in Windows 10/11 and Server 2019/2022; it only needs Group Policy settings to come into effect. High level steps are:
- Install the management components on management computers (i.e. extend the AD schema if you plan to store passwords in AD)
- Configure permissions (i.e. make sure only the right people can view passwords)
- Enable and configure LAPS by GPO (you can choose how to deploy this GPO, via AD or Intune; you can also configure password complexity & duration, and more)
✅ Good Example - Video: Managing local admin account passwords in AD and Azure AD (long - 20 min)Windows LAPS (legacy)
The legacy LAPS download includes a comprehensive operations guide, with step-by-step installation instructions. The high level steps were:
- Install the management components on management computers (i.e. SysAdmins)
- Install LAPS on computers to be managed - this can be done by GPO
- Create the AD attributes that will securely store the password
- Configure permissions (i.e. make sure only the right people can view passwords)
- Enable and configure LAPS by GPO (you can configure password complexity & duration, and more)
To view the password you can use the LAPS UI tool (included with the standard installer), view it in AD Users and Computers, or with PowerShell. You can reset the password with the UI tool or with PowerShell.
With more companies adopting BYOD policies, it is important for SysAdmins to be able to connect to Remote Server Administrative Tools (RSAT) like Active Directory Users and Computers (ADUC) in a secure way, even if their computer is not connected to the domain.
Note: You should make sure any personal devices connecting to your network are secure, with Intune or a similar solution.
RDP to the domain controller (don't do this!)
The least secure way is to use Remote Desktop Connection to make changes directly on the domain controller. Domain controllers should be locked down to only accept log ins from domain admin accounts - and should only be used when changes require these credentials.
Another option is to connect to a different computer or server that is on the domain, like a jump box. This is a more secure solution, but for many companies it adds infrastructure that is not necessary.
Windows Admin Center
Microsoft have a browser-based server management tool called Windows Admin Center. It is very useful for managing servers, and it can also be used to manage your AD environment - as well as DHCP, DNS and other Windows Server services.
Since the tool is browser-based, you only need to allow access to one port for HTTPS communication.
Read more about Windows Admin Center here: Do you use Windows Admin Center?
Running RSAT from a non-domain joined computer
While Windows Admin Center is a great solution, many SysAdmins prefer the extra functionality and classic interface of RSAT (Remote Server Administration Tools) in MMC (Microsoft Management Console) that you can easily run from a domain joined computer.
You can also use this if you have a domain-joined computer, but you need to use a different account to the one you log in with to access RSAT.
To get RSAT connected on a non-domain joined computer, there are some extra steps:
- Make sure you have the RSAT features you need: Install RSAT Features
- Run Command Prompt as Administrator
-
Run this command to open an empty MMC window (replace admin@domain):
runas.exe /netonly /noprofile /user:"admin@domain" mmc.exe - Go to File | Add/Remove Snap-in... to add the tools you need, e.g. ADUC, DHCP, DNS, GPO Management
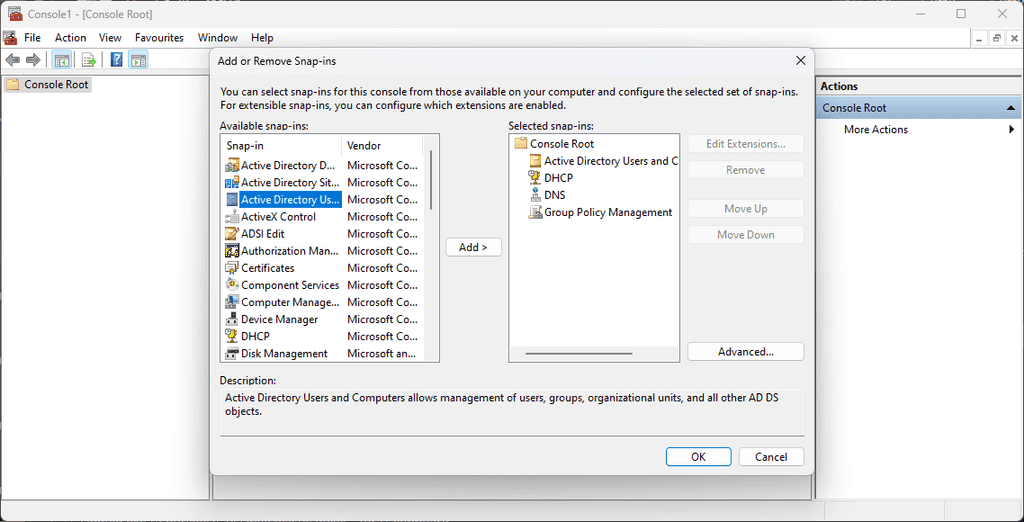
Figure: MMC | Add or Remove Snap-ins -
For ADUC (and possibly other tools), you will need to specify the domain to connect to. Make sure you tick the box Save this domain setting for the current console.
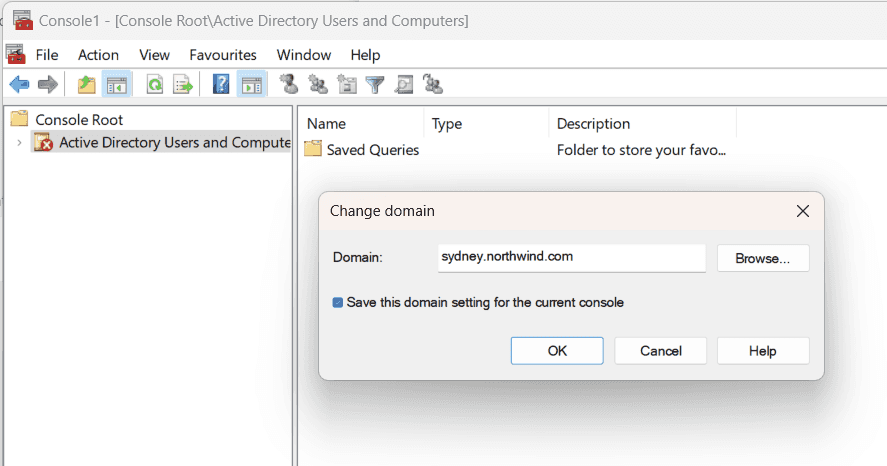
Figure: ADUC | Change domain - Go to File | Save As... and save the console somewhere appropriate, e.g. C:\work\rsat.msc
-
Create a batch file with this command - similar to the command above, but we specify the .msc file to use:
runas.exe /netonly /noprofile /user:"admin@domain" "mmc.exe "C:\work\rsat.msc"" - Save the batch file and run it as administrator.
- Your MMC window will open with your snap-ins ready to go!