Rules to Better Internet and Networks - 21 Rules
Networks are the lifeblood of any business. This is why we have developed a few rules for better Internet and Networks.
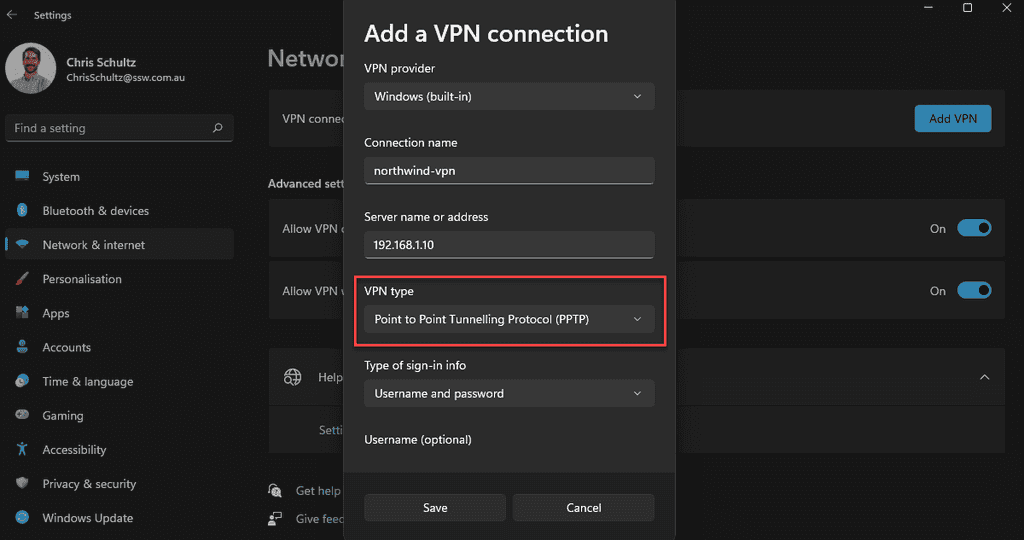
If you have a Remote Access VPN, it is important to ensure that the VPN is secure. VPNs are a common point of attack in cyber security incidents - if a bad actor can get into your VPN, they're in your network.
These days, the most important way to secure your VPN is to use MFA. The best way to set this up will depend on the VPN and current MFA solution you are using.
It is also important to make sure that your VPN uses a secure protocol. Previously PPTP was a popular method, but this is now a deprecated service as it can be hacked very quickly using online tools. It is recommended to go with a provider that uses SSL or IPSec protocols.
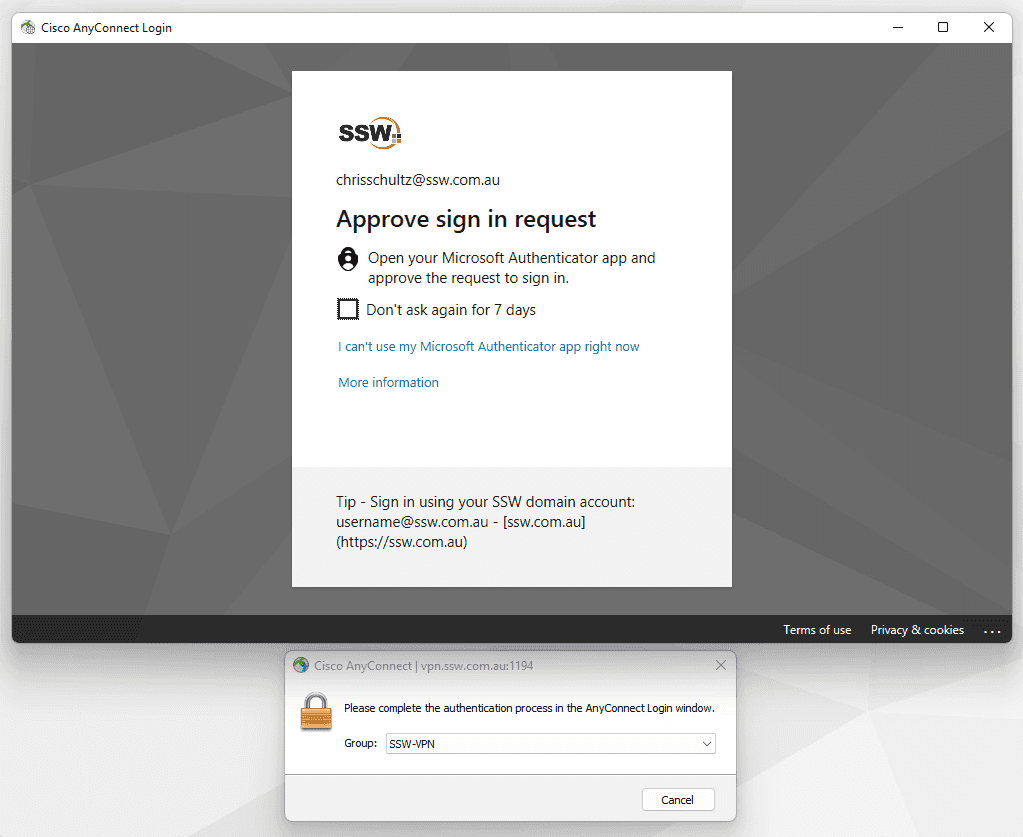
More information on Cisco AnyConnect
If you're using Cisco AnyConnect and Azure AD, it is easy to set up authentication through SAML - so your Azure AD MFA will be applied to any VPN logins.
The basic steps are:
- In Azure AD, setup AnyConnect as an Enterprise application
- In Azure AD, add the users that you want to have VPN access
- Configure your Cisco ASA to use SAML for VPN authentication
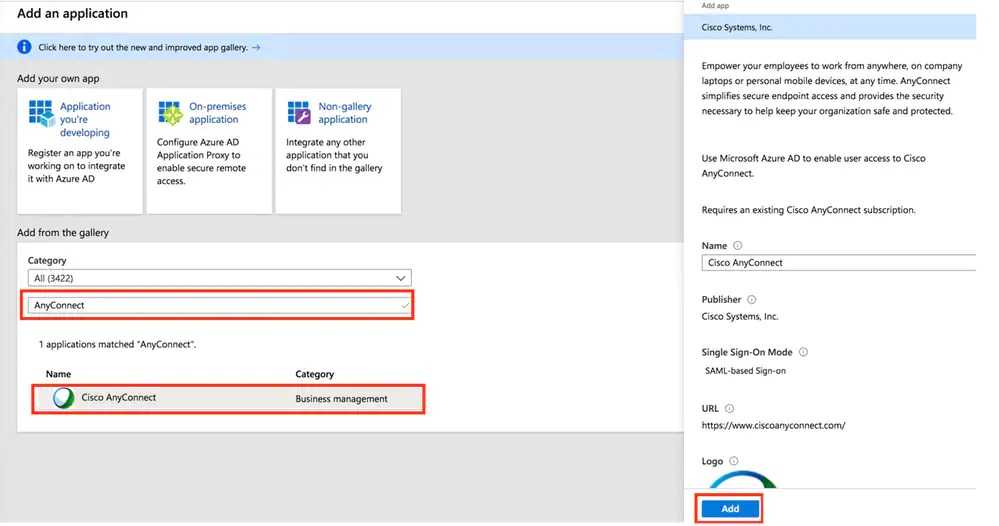
Figure: Adding Cisco AnyConnect as an Enterprise Application in Azure AD For more information, see Cisco's documentation here.
If you are going to install a service pack on a machine, moving a virtual server to another drive or doing any critical system level changes, make sure you back up your machine first. For virtualized machine, make sure you back up all related files, including vhd, avhd etc.
You should already assume there could be catastrophic failure after these kind of operations and you should always be prepared for them by having a full backup somewhere. This is especially important when you are working your production or critical servers.
w3dt.net supplies a DNS report tool which can help administrator to troubleshoot DNS issues with domains, name servers, SOA, and other information. We need to get all green ticks except for:
- Missing (stealth) nameservers
- Missing nameservers 2
Keeping networks and VLANs separated is an essential aspect of a robust security strategy. This is particularly true for less secure networks such as automation and HVAC systems, which are often targeted by cybercriminals looking to gain unauthorized access to the network.
The following guidelines can help system administrators maintain the separation of VLANs.
Define VLANs
Assigning different VLANs for different client types and services provides a logical division of the network. This will help ensure that each network is independent, even if they share the same physical infrastructure.
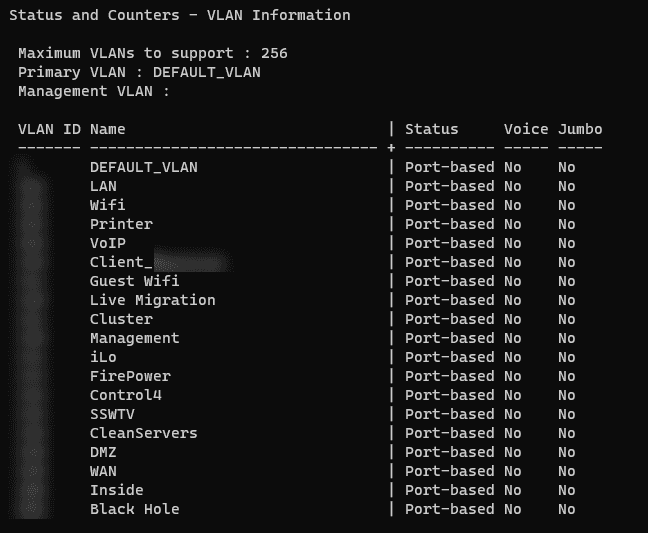
Figure: Separate VLANs on an Aruba switch Implement Security Measures
VLANs should be separated using access control lists and firewalls. Ensure that there are no unauthorized access points between VLANs and that the only devices that can communicate between VLANs are those that are authorized.
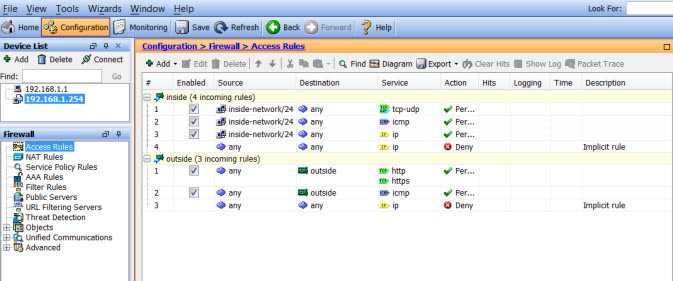
Figure: Cisco ASA | Access Rules By following these guidelines, system administrators can keep networks and VLANs separated while enacting security measures that will prevent unauthorized access to every part of the network. Thus, creating a safer and more secure network environment.
Have you ever faced a scenario where an unauthorized device is discreetly connected to an open port on your network switch, potentially intercepting sensitive data or disrupting critical services? This situation isn’t just theoretical - it can lead to serious security breaches, data theft, and system downtime if you do not restrict the MAC addresses allowed to connect.
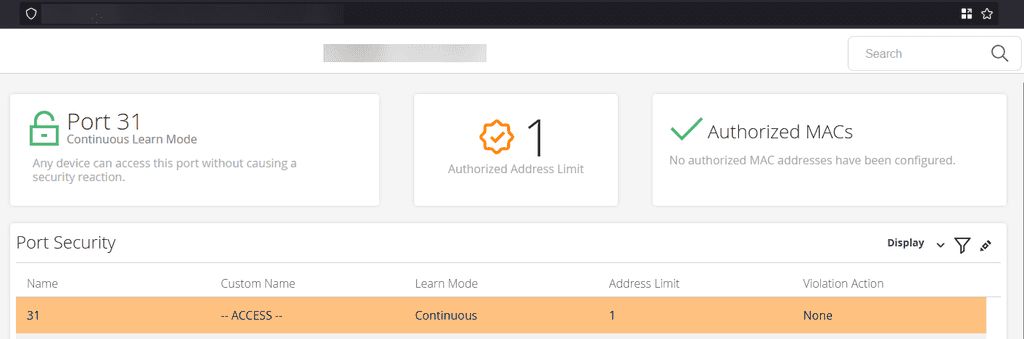
Figure: Bad example - An access port with continuous learn mode, meaning any device can connect to it and no security traps will be raised An open switch port accepts any device, allowing a malicious actor to connect and compromise internal systems.
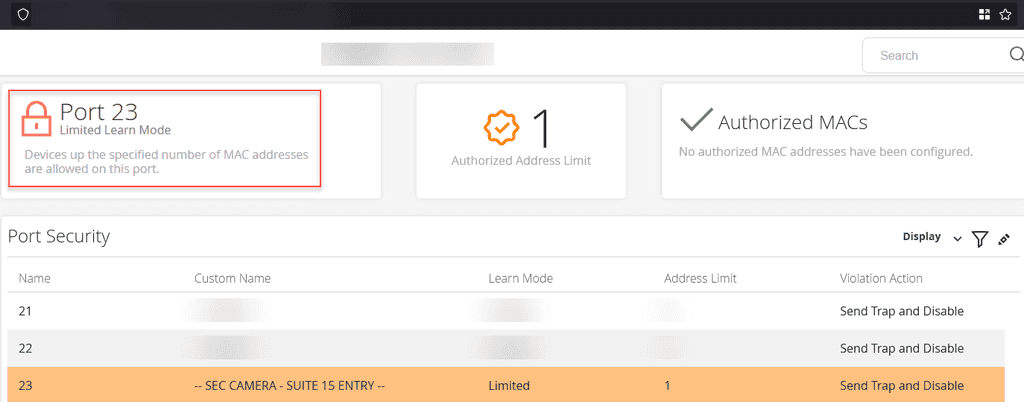
Figure: Good example - A switch port accepts only predefined MAC addresses, or is limited on the number of MAC addresses it can learn. Unauthorized devices are immediately blocked, safeguarding the network’s perimeter Benefits of limiting MAC addresses on network switches
- Increased security - Restricts unauthorized hardware from accessing sensitive resources
- Stronger perimeter - Keeps dangerous devices from infiltrating your network, especially at high-risk access points like camera ports
- Data protection - Maintains the integrity and confidentiality of your data by ensuring only trusted devices connect
Particularly Vulnerable: Camera Ports
Outdoor or easily accessible camera ports are prime targets, as attackers can physically connect rogue devices to these less protected areas. By setting static or pre-approved MAC addresses on these ports, you ensure only the intended camera is allowed—keeping bad actors out.
Together with other security standards like keeping your networks separated via Virtual LANs and using Intrusion Prevention Systems, your network should always be tested and protected against malicious actors in the wild.
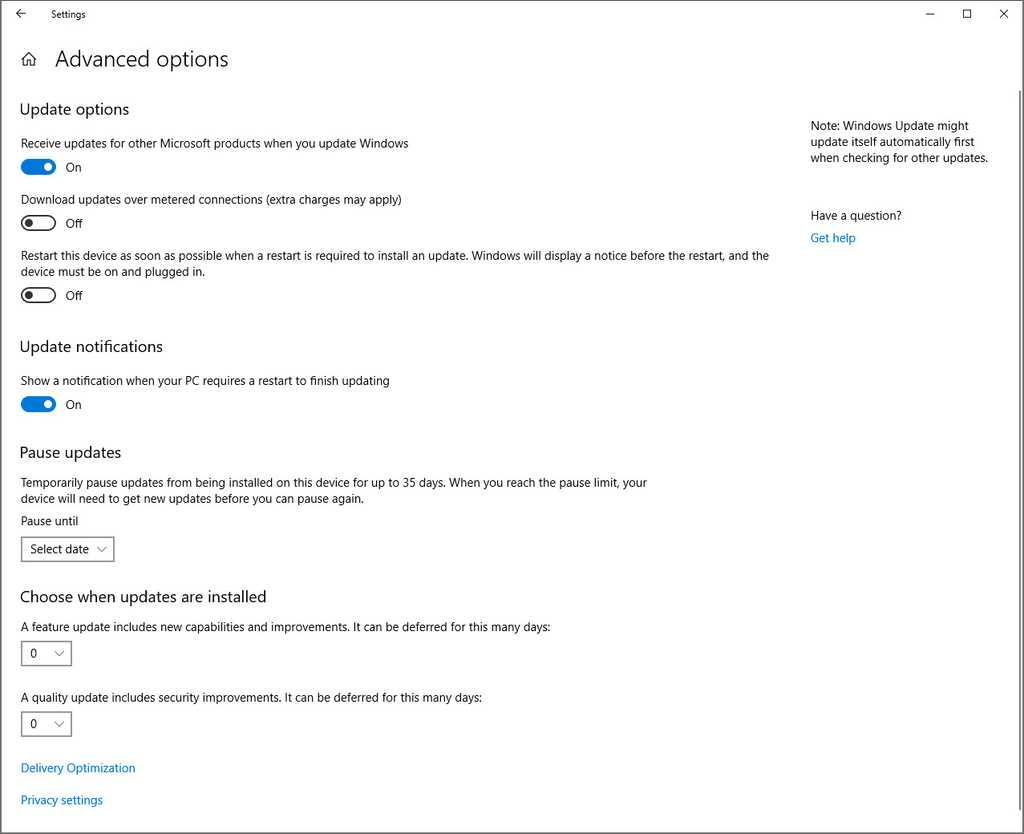
Microsoft Update is a service that allows for the periodic patching of system files to address known issues with Microsoft products. Originally called Windows Update, it was specifically focused on Operating System patches for Windows but has been expanded to include all Microsoft products and the name has changed to Microsoft Update, allowing the automated patching of non-OS software such as Internet Explorer and Microsoft Office.
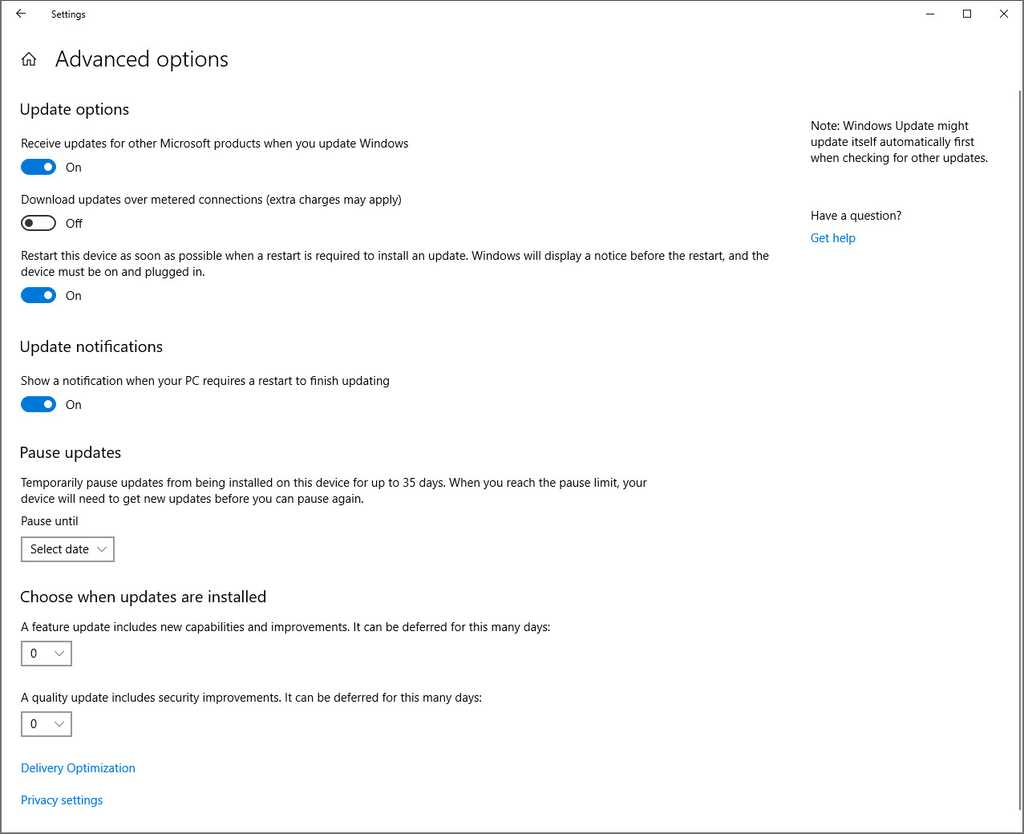
It is important to keep your machine up-to-date, but Windows Update Automatic installation can be somewhat intrusive to your workflow. There is nothing worse than getting Windows Updates installing during an important presentation. You should set Windows Updates to be installed manually.
Note: This is only for client machines, Windows Update for Servers should be handled differently. See Do you use Group Policy to manage your Windows Update Policy? for more information.
- Go to Start | Windows Update Settings | Advanced Options
- Set Restart this device as soon as possible... to Off
- Set Update Notifications to On.
If you have a system administrator who manages your organization’s infrastructure, it's recommended to get you system administrator to push this setting via group policy.
When we configure networks we give all computers in the company a naming theme like:
- Buildings
- Cars
- Countries
- Colours
- Fruits
- Vegetables, etc
At SSW we have adopted the animal kingdom.
Figure: We name the PCs and label them - this one is "Great Pyrenees" While you are attaching the label, it is also a good idea to affix a business card to the underside of the computer. This way if you lose your machine, anyone who finds it can easily contact you.
Having a very popular website is great. The only problem is where to host it. If you host it in your local country then it is very fast for your local market but what about the market on the other side of the world? The solution to this is to use a Content Delivery Network (CDN).
The solution is to have an origin server (can be multiple for loadbalancing) and Content Delivery Nodes in locations that have many users accessing the website. Users will be delivered content from the closest Node. This is possible with the help of Bind DNS server and a list of IP addresses and the country of origin.
CDN is provided by many cloud providers such as WPEngine, Azure, CloudFlare but can also be achieved by using opensource software such as JSDelivr, Cdnjs and many others.
It can also be achieved using IIS Outbound Rewrite rules. For example
https://ssw.com.aucould be change tohttps://us.ssw.com.auand be directed to another IIS server.When you are connected to the company's network, you should complete the following procedure if you want to setup a printer server.
For Windows Server
Steps to add a printer to Active Directory:
- In Windows Run | Type "printmanagement.msc" | Hit Enter
- Right-click 'Print Server' | Choose 'Add/Remove Servers' | Add IP address or computer name | Finish
or
Right click the 'Print Server' | Add printer | Choose the best option (e.g TCP/IP) | Put the IP address of the Printer | Finish
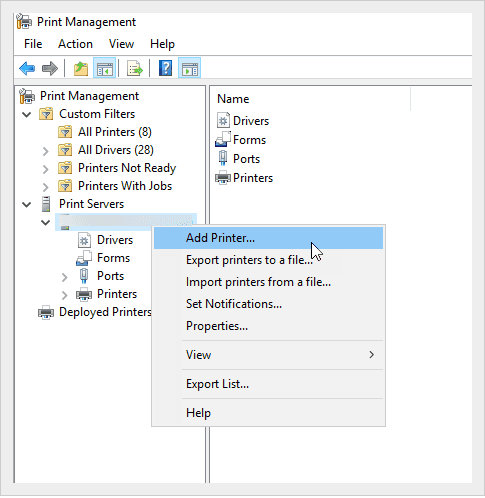
Figure: Add Print servers to AD - Add DNS entry for your print server (e.g \printer) to make it friendly for the users to find
Note: Another method is using a Universal Printer in Azure https://azurescene.com/2020/04/10/how-to-configure-universal-print/
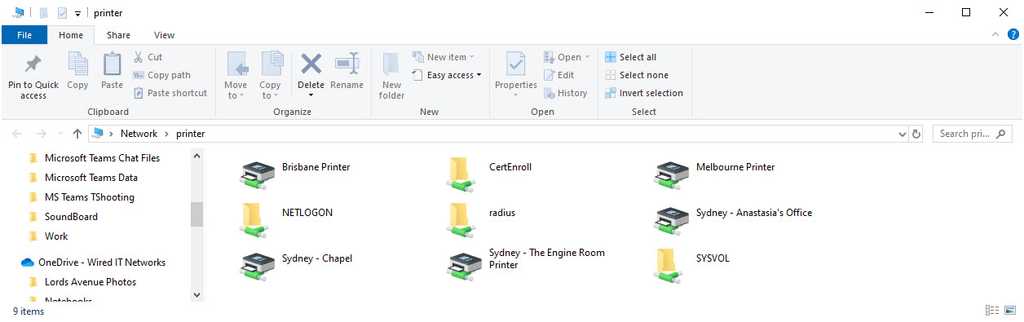
Finding the Printers
Now your users can find the printers by doing the following:
- In the File explorer | Type \printer on the address bar to show all the printers connected to the server
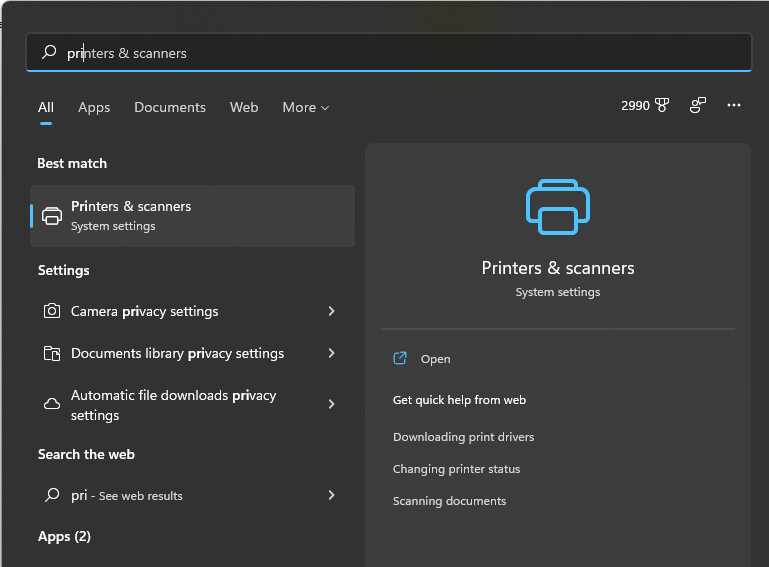
Figure: Bad example – Windows 11 | Printers & scanners - Users won’t see all the printers by default - Double click on your printer name to connect/add it. Follow prompt to finish the printer driver installation
When an employee leaves or a domain account expires, disable the account, never delete it, as:
- Some LOB application such as CRM maintain a reference to the AD domain user GUID
- During the migration or restoration of CRM, users stored in the database are verified against AD and problems may occur if they no longer exist
We've seen this happen too many times - a user wants to do something on a network server machine, and because the user hasn't got a profile setup on that machine, he end up using the Administrator password to log on as administrator.
This is not a good thing because:
- We cannot tell who currently is logged in remotely, so if another developer wants to change something on the server, we can't work out who is on it.
- This is particularly the case where a lot of the servers don't allow multiple concurrent users, so we need to know who to disconnect or kick to free up a remote connection license.
- A lot of applications are installed as 'administrator', and no one end up remembering what they installed, and thus the administrator profile is loaded with applications that most people don't use.
- If you check in/check out files from Source Safe, it may end up using the administrator account - which means we can't work out who made a change in source safe.
So log on using your own domain account.
This is how you free up more disk space on servers:
- Check sql backups
- Check sql logs
- Use TreeSizePRO to find disk spaces issues
- Use CCleaner to automatically clean any temporary or junk files on the server
You should use virtualized standalone servers because:
- If one server goes down it does not affect other servers (e.g. a centralized SQL server fails and brings down: CRM, TFS, Reports, Web Server)
- You can just copy the VPC to another computer and it just works, no need to worry about reconfiguring the SQL connection string or web services
- You can just backup the VPC
However, you should scale out your servers if:
- You want the best performance (e.g. A different server for SQL backend and Web frontend)
Some of the network services, like TFS/Exchange/Database are essential for our business and people will not be able to work if any of these services is down or inaccessible.When such thing happens, the first thing you need to do is to send notification to SysAdmins so they can start investigating the problem, and you should cc your project manager because those issues will stop you getting tasks done.
ANAME record (also known as A record) is an alias record that allows you to map the apex record or any other record within your domain to a target host name, essentially a CNAME record for the apex record.
The ANAME record is especially useful for when you have multiple domain names and your website is hosted by a provider that changes it's IP Address, this does happen quite regularly with WPEngine. Many DNS service providers do not support ANAME record, however, DNSMadeEasy has made this service available.
Configuring ANAME is as easy as configuring CNAME.
Let's have a look at DNS records for adamcogan.com.au, DNS records contains apex record for adamcogan.com.au and www.adamcogan.com.au. The apex record uses ANAME, while CNAME for www.adamcogan.au - now we will never have to worry about updating these records, they will follow the DNS records of adamcogan.com .
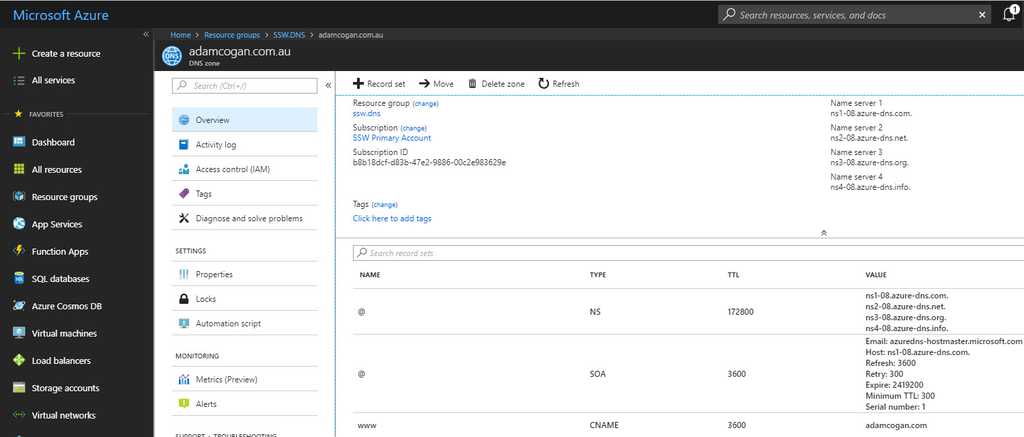
Figure: Example DNS entry from Azure DNS Cisco's FirePower module is able to automatically get a list of suspicious IPs from Cisco, however the IPs that are attempting to break into your network may not be the same as Cisco's recommended Blacklist. That is why it is important to have your own IP Blacklist.
This needs to be an internally accessible webpage that the FirePower module can access and use as it's Blacklist. An example script for this can be found on GitHub.
This script gathers IP Addresses from well-known internet lists, sanitizes them of internal IP addresses and adds them into a text document that is then accessible by the Cisco FirePower module.Alternatively, you could also get failed login attempts and compare them against multiple IP reputation sites. If it looks suspicious on 3 or more sites, add it to the text document above.
When purchasing new network hardware you should always choose the most reliable option.
We have discovered that:
Firewalls
1. Cisco ASA is the best. Cisco has built a lot of trust and a large community of backers over the years by providing an extremely solid product. Finding support and assistance with Cisco devices is much easier than most vendors due to the sheer size of the community. Also pushing it to the lead are advanced features like:
- Malware Protection
- Application Control
- FirePOWER Threat Defence
- Centralised Firewall Management Center
2. pfSense is the second best. One of the most used firewalls and for good reason. This Open Source firewall offers similar features to the leading providers of firewalls but comes in at a fraction of the price since the software is free and only requires you to purchase the hardware to run it. This gives you the ability to have an extremely good firewall at a fraction of the price.
Switches
1. HPE is the best. HPE Switches now rebranded as Aruba Switches have provided a strong product for many years. The feature that really pushes this ahead of the game is the reliability of the hardware as well as a lifetime warranty on hardware with next day replacement at no additional cost.
2. Cisco is the second best. A leading product for many years however comes at a much larger cost than HPE/Aruba and usually contains ongoing license fees for support. But is a very reliable and feature rich product.
3. Extreme has great Switching and Wireless products that are excellent for enterprise environments
Access Points
1. Ubiquity is the best. Quickly becoming the leading AP used in the industry it offers a rich cloud management software allowing ease of management over multiple sites and countries. Unifi Access Points are easy to manage and install and can be upgraded and provisioned with the touch of a button. With new features being released regularly and prices much lower than Cisco and Aruba it is hard to not see why this is the best.
2. Cisco/Aruba is the second best. Offering many features and used on many large projects such as the University of Wollongong for Cisco and KFC for Aruba they offer truly tried and tested hardware. These products do come at a higher cost and requires a lot more skill and time to manage and really only come into the spotlight on large scale projects.
To help with automation (e.g. SophieBot) you can use the MAC address of your mobile device to match when it joins the company Wi-Fi. This allows you to:
- Automatically log when you come in or out (See Do you know the best way to see if someone is in the office?)
- Announce your presence to the rest of the office
-
Get statistics and analytics: E.g. Who travels the most? Or which city uses In-And-Out the most?
TODO: Uly
Here is how to find your MAC address:
iPhone
- Open the Settings app
- Navigate to General | About
- Look for WiFi Address
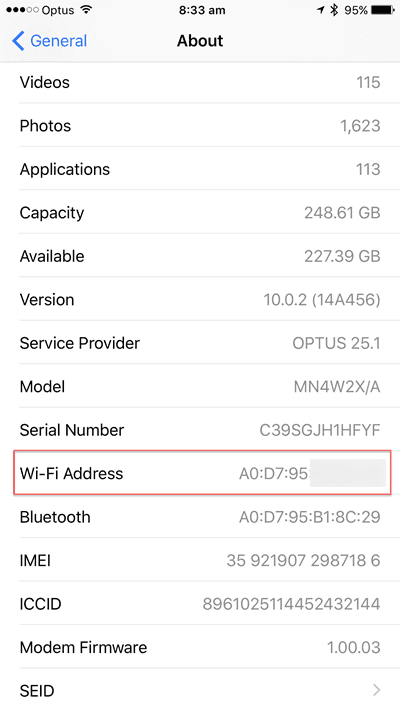
Figure: MAC address on an iPhone Android Phone
- On the Home screen, tap the Menu button and go to Settings
- Tap About Phone
- Tap Status/Hardware information
- Scroll down to see your WiFi/MAC address
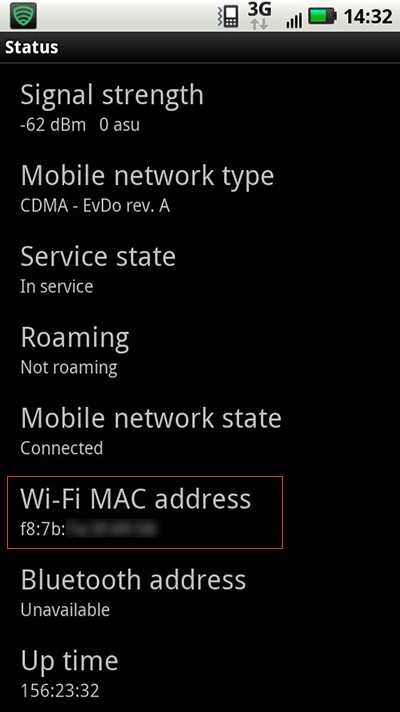
Figure: MAC address on an Android Network Intrusion Prevention Systems (IPS) can assist with network security by automatically detecting network attacks and stopping them before they become an issue.
Most business firewalls have some sort of IPS/IDS system built into them. Cisco has FirePower and PfSense has Snort. Both will assist in watching for suspicious activity and DDoS attacks, blocking traffic where necessary.
Both FirePower and Snort can get automatic updates from the internet so they remain at the forefront of new emerging attack strategies, so it is important to ensure that the associated module has internet access to remain up to date.
Depending on your environment you may want to enable inspection of all traffic, however this may slow data transfer, but it may be important depending on the data your company is dealing with. Otherwise it is recommended that WAN to LAN traffic is being inspected only.
Have you been in a scenario when you look at a website in your phone and it works. Meanwhile, one of your colleagues is looking at it in their PC and they get a response saying this site doesn't exist. That's probably a DNS (Domain Name System) issue.
DNS is akin to the internet's phonebook. It's easy to remember a website's name, like
www.ssw.com.au, but computers and networks need numerical IP addresses to access websites. DNS translates human-readable domain names to machine readable IP addresses.DNS explained
Video: Everything You Need to Know About DNS (5 min)Understanding DNS is crucial for troubleshooting connectivity issues, optimizing network performance, and ensuring secure internet navigation
When you type
www.ssw.com.auinto your browser, the process to translate this human-readable domain name into a machine-readable IP address involves several steps and servers in the Domain Name System (DNS). Here's a detailed breakdown:- Domain Name Input - You enter
www.ssw.com.auinto your web browser. - Browser Checks Cache - First, your browser checks its own cache to see if it has recently resolved the IP address for
www.ssw.com.au. If it finds the IP address there, it skips the remaining DNS steps and proceeds to connect to the web server. - Operating System Cache Check - If the browser cache doesn't have the IP address, the query moves to the operating system's DNS cache. If the operating system (OS) has the IP address cached, the DNS lookup process stops here, and the browser uses this IP address. If not, the process moves to the next step.
- DNS Resolver Query - The query is sent to a DNS resolver, typically operated by your Internet Service Provider (ISP). The resolver checks its cache; if the IP address is there (and still valid based on its TTL), the process ends, and the IP is returned to your browser. If not, the resolver queries a root nameserver.
- Root Nameserver Query - The DNS resolver contacts one of the root nameservers. The root server doesn't know the IP address for
www.ssw.com.aubut knows where to direct queries for.audomains. It responds with the address of the TLD nameserver for.au. - TLD Nameserver Query - Next, the resolver contacts the
.auTLD nameserver. This server manages information for.audomains but doesn't store individual IP addresses. Instead, it knows which authoritative nameserver handlesssw.com.au. It responds with the address of this nameserver. - Authoritative Nameserver Query - The resolver then queries the authoritative nameserver for
ssw.com.au, which has the actual IP address forwww.ssw.com.au. This server responds with the IP address of the web server hosting thessw.com.ausite. - Resolver Caching - The DNS resolver caches the IP address of
www.ssw.com.auwith the corresponding TTL. This caching helps speed up future requests to the same domain. - Browser Connection to Web Server - With the IP address now known, your browser can establish a connection to the web server hosting
www.ssw.com.au. It sends an HTTP request to the server asking for the web page associated withwww.ssw.com.au. - Web Server Response - The web server processes the request and sends the requested web page back to your browser, which then displays the content to you.
Each of these steps involves complex interactions between your computer, various DNS servers, and the final web server hosting the content you wish to access. This process, although it might seem lengthy, happens within milliseconds, allowing for the quick loading of web pages.
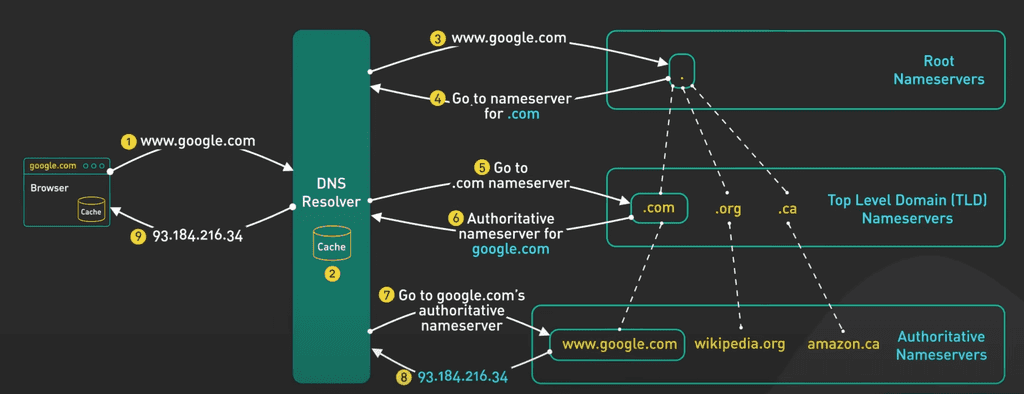
Figure: DNS - finding the correct authoritative nameserver Image source: ByteByteGo's DNS Video
Hierarchical Structure of Domain Names
Domain names are structured hierarchically, with the right-most component being the top-level domain (TLD). In the domain name
www.ssw.com.au:.auis the country-code top-level domain (ccTLD) for Australiacom.auis considered a second-level domain within the.auccTLD. It's commonly used by commercial entities in Australiassw.com.auis a domain registered by an entity (in this case, SSW) within thecom.auspacewww.ssw.com.auincludes a subdomain (www) of thessw.com.audomain
How DNS Knows
com.auis a TLDIn essence, DNS doesn't treat
com.auas a single TLD but rather as a combination of a second-level domain (com) under the.auTLD. The distinction comes from the DNS hierarchy and the namespace management:- Root Nameservers: At the top of the DNS hierarchy are the root nameservers. They have the information necessary to direct queries to the TLD nameservers.
- TLD Nameservers: Each TLD, like
.com,.net,.org, or a country-code TLD like.au, has its own nameserver(s). When a query reaches this level, the TLD nameserver directs the query to the appropriate second-level domain nameserver, if applicable. - Registry and Registrar: The registry for a TLD manages the domain names within that TLD. For example, the registry for
.aumanages all domains ending in.au, includingcom.au,org.au, etc. When someone registers a domain likessw.com.au, they are registering a second-level domain within the.auTLD. The registry ensures that each domain name is unique within its namespace. - Authoritative Nameservers: For a given registered domain, like
ssw.com.au, there are authoritative nameservers that know the IP addresses for subdomains (likewww.ssw.com.au).
Direct Browsing to a Second-Level Domain
You can browse to a second-level domain if it is set up to host content. For example, if
com.auwere registered as a domain with its own website, you could browse to it directly. However,com.auis reserved for structuring domain names within Australia and is not used as a standalone website. This is managed through DNS policy and registration rules set by the domain registry responsible for the.audomain space.In summary, DNS distinguishes between different levels of domains through its hierarchical structure, managed by a combination of root, TLD, and authoritative nameservers. The ability to browse to a domain depends on whether it is registered and configured to host content, regardless of whether it's a TLD, a second-level domain, or lower.
Common DNS record types
In the context of DNS (Domain Name System), a "type" refers to the kind of DNS record in a DNS server's database, here are some common ones:
Type Function Common Example Address Record (A) Maps a domain to an IPv4 address example.commaps to93.184.216.34IPv6 Address Record (AAAA) Maps a domain to an IPv6 address example.commaps to2606:2800:220:1:248:1893:25c8:1946Canonical Name Record (CNAME) Maps a domain to another domain name (aliasing) www.example.comaliases toexample.comMail Exchange Record (MX) Specifies mail servers for a domain example.commail handled bymail.example.comName Server Record (NS) Delegates a subdomain to a set of name servers sub.example.comdelegated tons1.example.comPointer Record (PTR) Maps an IP address to a domain (reverse DNS) 34.216.184.93reverses toexample.comStart of Authority Record (SOA) Stores administrative information about a zone example.comSOA record indicatesns1.example.comas primary NSService Locator Record (SRV) Specifies services available in a domain _sip._tcp.example.compoints to SIP server atsipserver.example.comport 5060Text Record (TXT) Holds text information for external sources to read example.comuses a TXT record for SPF:"v=spf1 include:_spf.example.com ~all"- Domain Name Input - You enter